¶ Nomid MDM Portal Manual
| Application or layer: | Version | Last update date |
|---|---|---|
| Portal | V1.4.3 | 03/28/2024 |
| Document | V1.1.1 | 15/01/2025 |
| Language | en_US | - |
¶ Login
¶ Change language
MDM Nomid Tech provides an interface in the following languages:

- Português: pt-BR
- Español: es-ES
- English: en-US
¶ Dashboard
¶ Totalizations
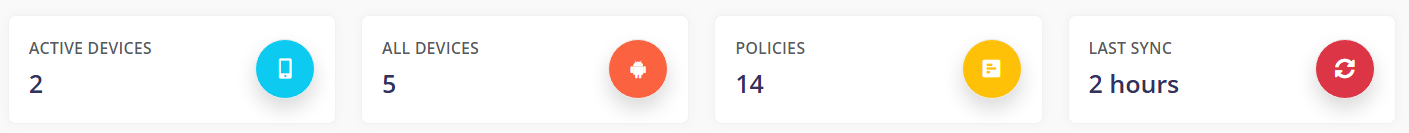
¶ Active devices
It shows the quantity of active devices.
¶ All devices
It shows the total number of devices managed by the solution.
¶ Policies
It shows the number of policies created on the account.
¶ Last sync
Time has elapsed since the last synchronization.
¶ Graphics
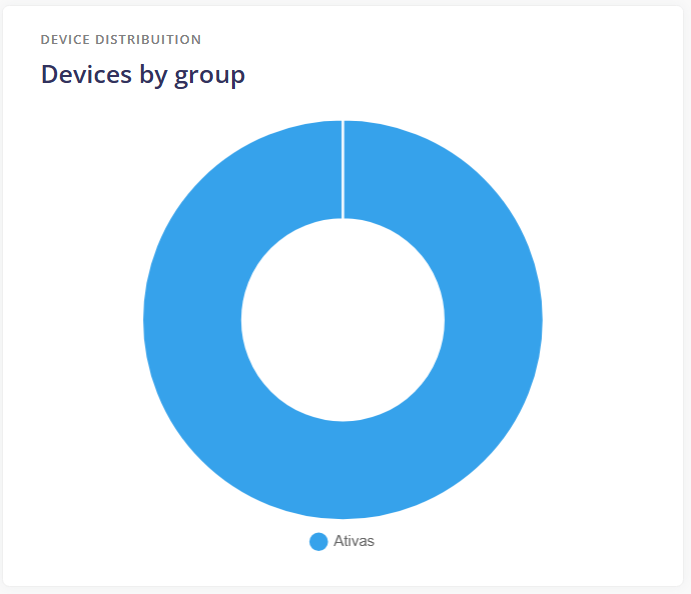
¶ Devices by status
Number of devices per Status.
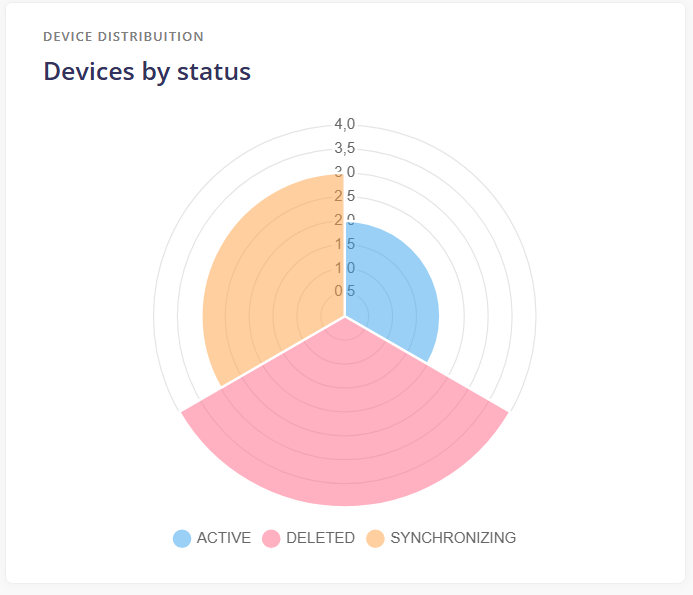
- Active: Active devices reporting correctly and managed by the MDM.
- Inactive: Devices that no longer report or are under MDM management.
- Delected: Devices that have already received the deletion or discontinuation order.
- Synchronizing: Devices that are in the phase of policy synchronization and information collection.
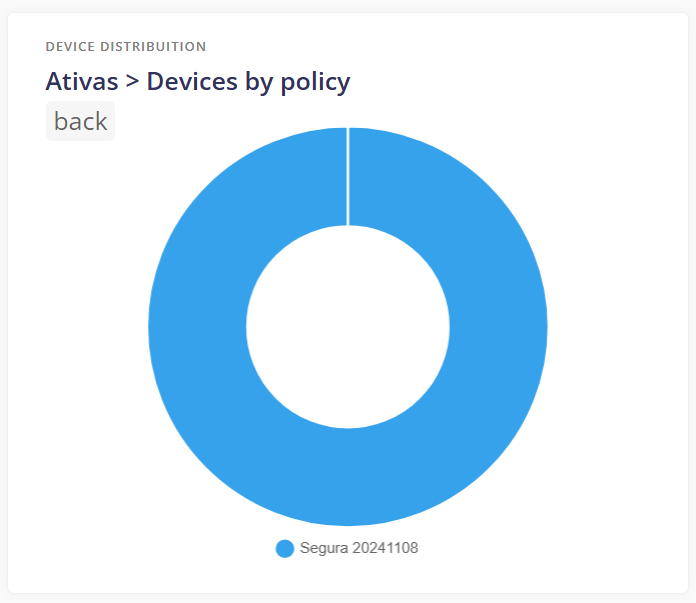
¶ Devices by policy
Number of devices per policy group that allows for detailing of the number of devices per policy.
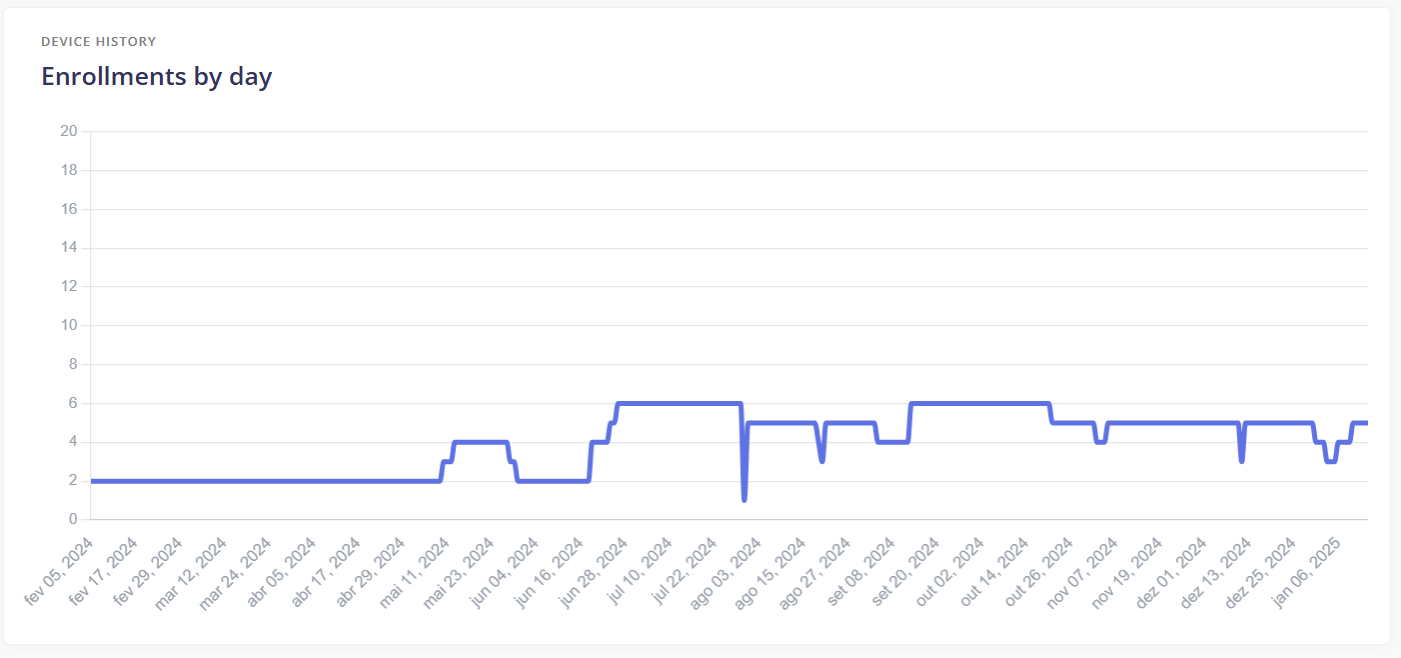
¶ Enrollments by day
History of the number of managed devices.
¶ Chatbot
¶ Support ChatBot
Chatbot activation button: Allows users to start an interaction with the chatbot by opening a chat window for communication.

Support chatbot dialog window: Displays the interaction between the user and the chatbot, allowing the user to send messages and receive automated responses or instructions to speak with a human representative.
¶ Menu
¶ Lateral menu
- Dashboard: Quick access to an overview and summary of key metrics and information about the MDM.
Management
- Devices: Management and monitoring of devices registered in the MDM.
- Policies: Configuration and enforcement of security and usage policies for the devices.
- Company: Information and settings related to the company using the MDM.
Enrollment
- New device: Process for registering a new device in the MDM.
- New policy: Creation and implementation of new security and usage policies.
- Zero Touch: Process for registering devices without manual intervention, automating the initial setup.
In the bottom right corner, there is a blue button used to expand or collapse the menu, represented by an arrow.
¶ Devices
¶ Search
The search will be carried out in the fields: Name, Description, Brand, Model, Status, IMEI, Serial Number, applied Policy, System ID, operational system and Tags.
¶ Synced until
It will filter out devices that has synchronized after the specified date.
¶ Send Report
Button that causes the search result to be exported and sent to the requester's email.
¶ List of enrolled devices
Table: Table listing all managed devices that allows you to search and navigate to device detail.
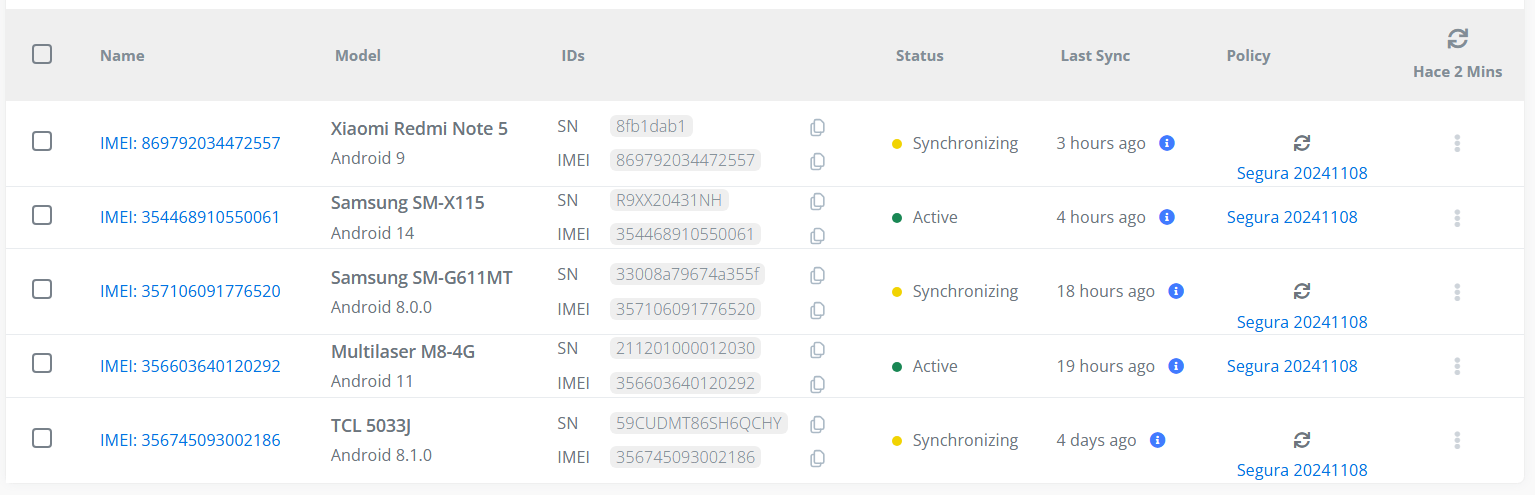
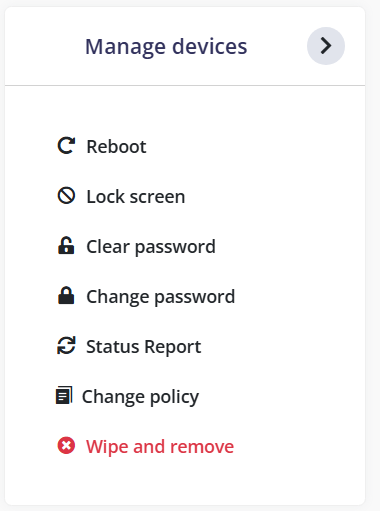
¶ Manage devices actions:
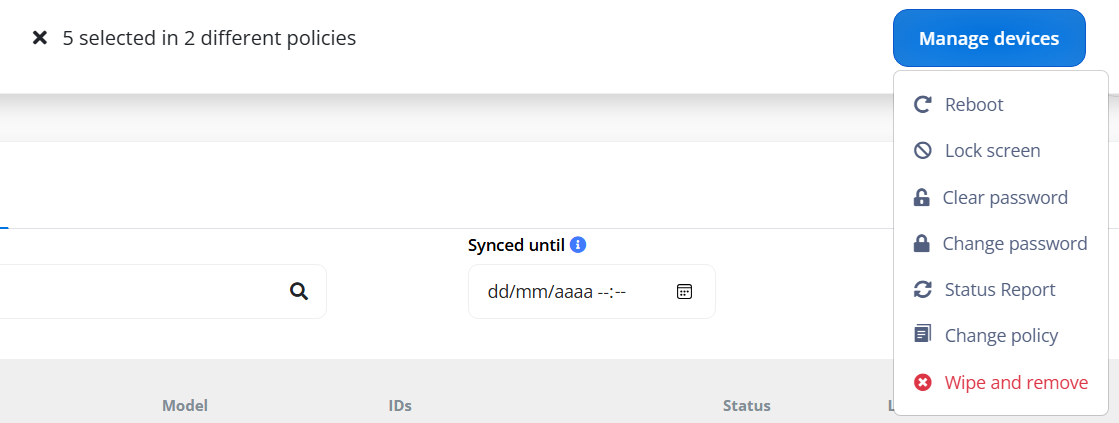
Manage devices mass actions:
Manage devices actions:
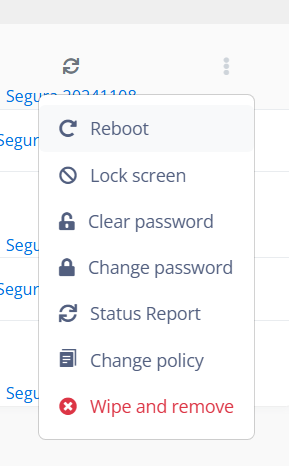
¶ Reboot
Allows remotely rebooting the device. This can be useful for applying updates or resolving technical issues.
¶ Lock screen
Allows remotely locking the device's screen. This can be used to secure the device if it is lost or stolen.
¶ Clear password
Allows remotely clearing the device's screen lock password, pattern, or PIN. This can be useful if the user forgets their unlock password.
¶ Change password
Allows remotely changing the device's screen lock password, pattern, or PIN. This can be used to enhance the security of the device.
¶ Status Report
Allows obtaining a report of the current status of the device, including information on settings, installed apps, and compliance with policies.
¶ Change policy
Allows changing the management policies applied to the device. This can be used to update security settings, app restrictions, or other policies.
¶ Wipe and remove
Allows wiping all data from the device and removing it from management. This is useful when a device is lost, stolen, or no longer needed.
¶ Device sheet
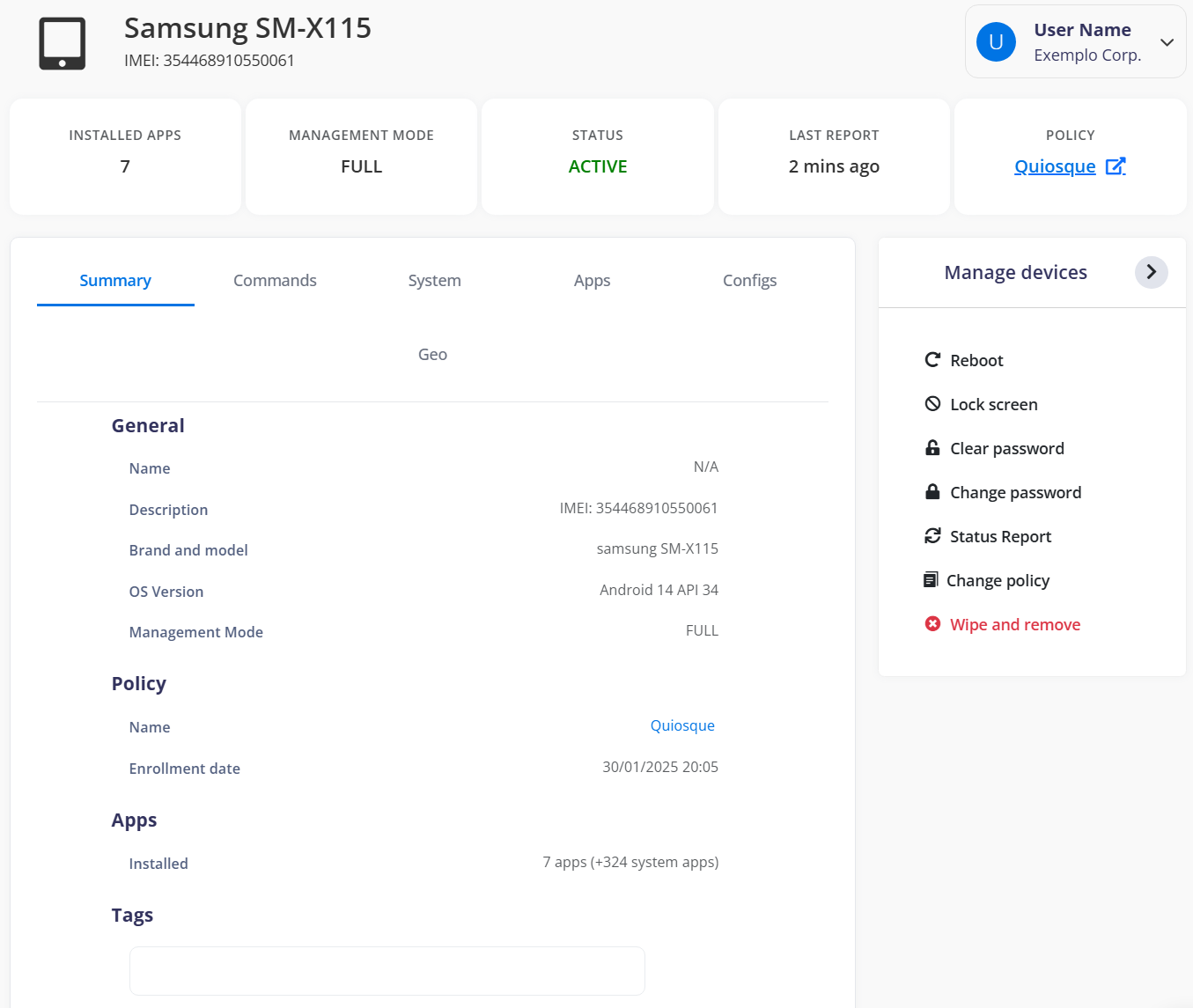
The equipment's datasheet displays all the device details, including its name and a summary, allowing navigation through all the device details.
¶ Brief
Name and individualization number:
Instaled apps: Total the number of applications installed on the device that are not directly related to the system.
Management Mode:
Status: Shows the device status.
Last Report: Shows the date and time of the equipment's last synchronization.
Policy: Shows under which policy the device is being managed.
¶ Summary

¶ General

Name: Refers to the name of the device, which can be set by the administrator or the user.
Description: It displays the device description information and contains relevant information for the individualization and recognition of the device.
Brand and model: Indicates the brand and model of the device. For example, "Samsung Galaxy S20".
OS Version: Refers to the version of the Android operating system running on the device.
Management Mode: Indicates the management mode of the device, such as "Profile Owner" for devices managed with a work profile or "Device Owner" for fully managed devices.
No field of the device record is editable except for the tags.
¶ Policy

Name: Shows the name of the policy that is managing the device.
Enrollment date: Shows the date of implementation of the policy.
¶ Apps

Installed: demonstrates the number of applications installed by the user and the number directly related to the system.
¶ Tags
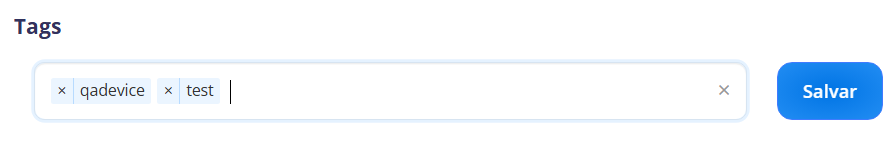
The only field that allows the entry of information to add details to the device, these details can be used in searches related to the device and receive automatic tagging information. For example, geofence marks the assets that have crossed the geographical boundary by adding a "geofence" tag to the device.
¶ Commands

Command history:
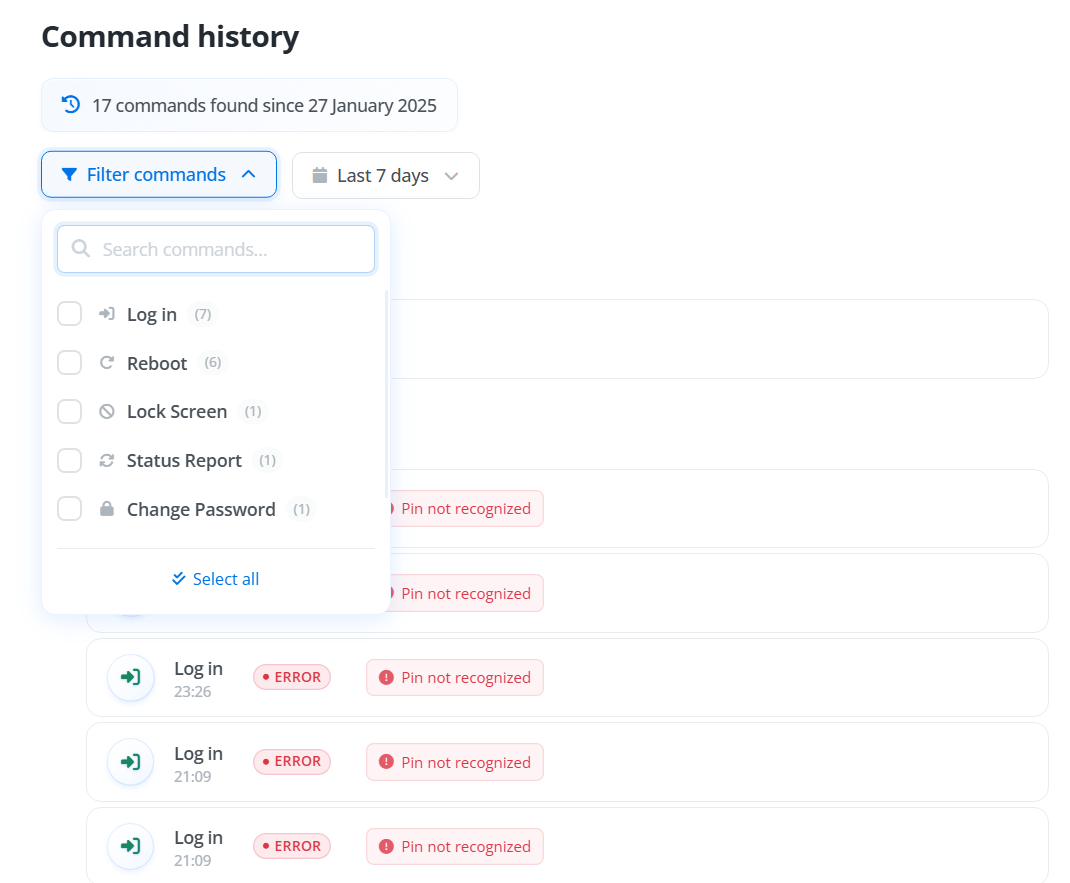
Commands:
¶ System

¶ General

System ID: The unique identifier of the system.
Name: The name of the device or system.
Description: A description of the device or system.
Status: The enrollment status of the device in the enterprise mobility management system, indicating whether it is enrolled and managed by the system.
OS Version: The version of the Android operating system being used on the device or system.
¶ Hardware

Brand: Represents the brand of the device. For example, Samsung, Google, LG, etc.
Manufacturer: Indicates the manufacturer of the device. It is usually similar to the brand, but in some cases, it may be different if the device is made by a different company from the brand.
Model: Specifies the exact model of the device. For example, Pixel 4, Galaxy S20, etc.
Baseband: Refers to the firmware version of the device's modem. It is important for connectivity and can be used to diagnose network problems.
Chip: May refer to the chipset or processor of the device. For example, Qualcomm Snapdragon 865, Apple A13 Bionic, etc.
Battery level: Indicates the current battery level of the device, usually as a percentage.
RAM: Represents the amount of RAM available in the device, usually measured in gigabytes (GB).
Storage: Indicates the total storage capacity of the device, usually measured in gigabytes (GB) or terabytes (TB).
Serial number: Refers to the unique serial number of the device, used for identification and tracking.
¶ Network

MEI 1 (Default): Refers to the primary International Mobile Equipment Identity (IMEI) of the device. It is a unique number used to identify mobile devices and can be used to track or block the device in case of theft.
Carrier 1: Indicates the mobile carrier associated with the first SIM card of the device. For example, Verizon, AT&T, T-Mobile, etc.
Phone number 1: Refers to the phone number associated with the first SIM card of the device.
IMEI 2: Refers to the second International Mobile Equipment Identity (IMEI) of the device, used in devices that support two SIM cards.
Carrier 2: Indicates the mobile carrier associated with the second SIM card of the device.
MEID: Refers to the Mobile Equipment Identifier (MEID), a unique identification number used to identify mobile devices on CDMA networks.
MAC address WiFi: Represents the MAC (Media Access Control) address associated with the Wi-Fi interface of the device. It is a unique identifier used for communications on local networks.
¶ Config

Unknown sources enabled: Indicates whether the installation of apps from unknown sources is enabled on the device. If enabled, users can install apps outside of the Google Play Store.
Encrypted: Refers to the encryption status of the device. Indicates whether the data stored on the device is encrypted for security.
Encrypted status: Provides more detailed information about the encryption status of the device, such as "enabled", "disabled", or "in progress".
Is secured: Indicates whether the device is secured by some form of screen lock, such as PIN, pattern, or password.
Developer mode enabled: Shows whether developer mode is enabled on the device. Developer mode allows access to advanced options and debugging tools.
ADB enabled: Indicates whether USB debugging through Android Debug Bridge (ADB) is enabled. USB debugging allows communication between the device and a computer for development purposes.
Verify apps enabled: Shows whether app verification is enabled. This setting helps protect the device from potentially harmful apps by checking them before installation.
Security posture: Refers to the overall assessment of the security posture of the device, taking into account various security settings and policies applied.
¶ Apps
¶ Installed apps
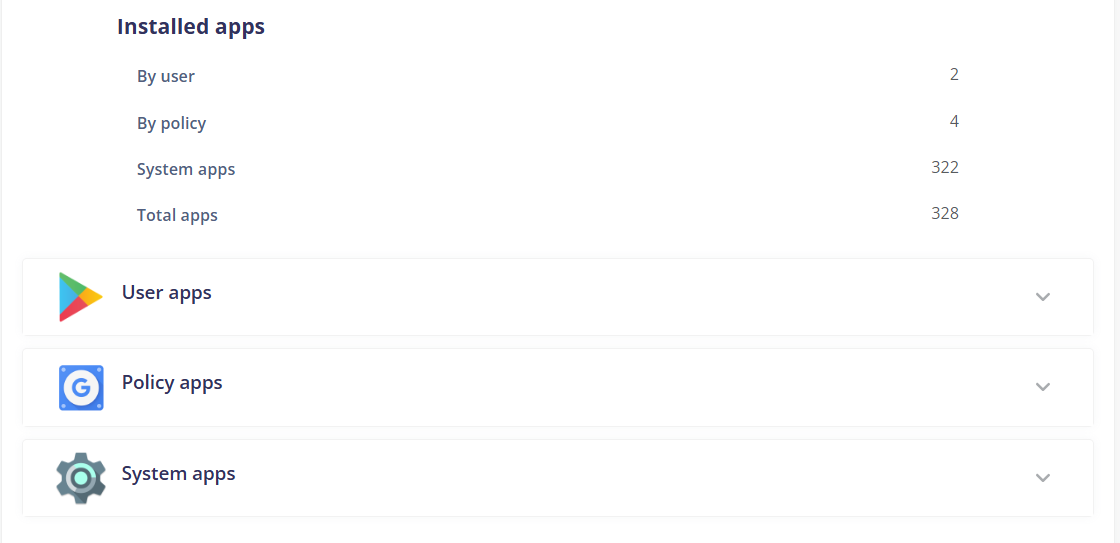
Lists all the apps installed on the device, including system apps and apps installed by the user or by management policies.
By user: Lists the apps installed by the user directly on the device.
By policy: Lists the apps installed on the device through mobile device management (MDM) policies or app management (MAM) policies.
System apps: Lists the system apps pre-installed on the device.
Total apps: Indicates the total number of apps installed on the device, including system apps, user-installed apps, and policy-installed apps.
Apps details: Provides details about the installed apps on the device, such as package name, version, granted permissions, data usage, and other relevant information.
¶ Config

¶ Applied policy
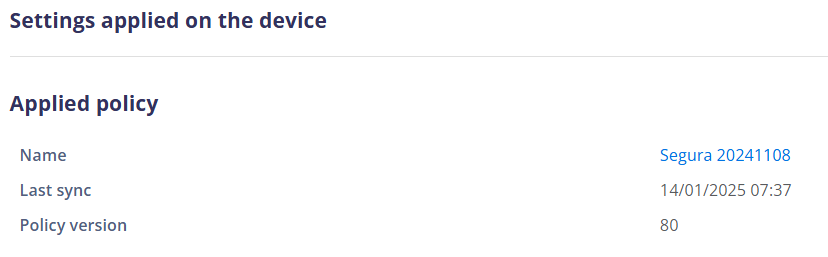
Name: Shows the name of the policy that is managing the device.
Enrollment date: Shows the date of implementation of the policy
Compliance:
Policy version: Shows the version of the policy applied on the device for easy comparison with the current version of the policy.
¶ Zero-Touch:

¶ Geo

¶ Location
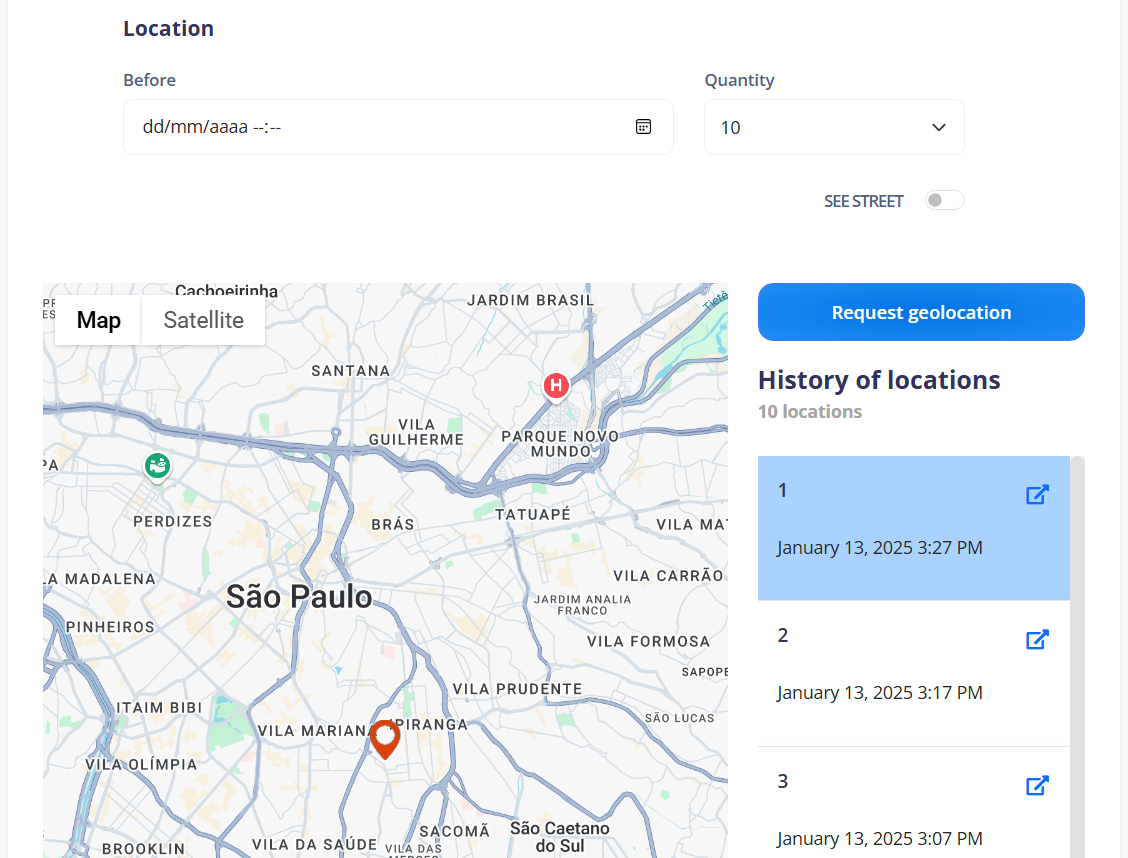
Date control:
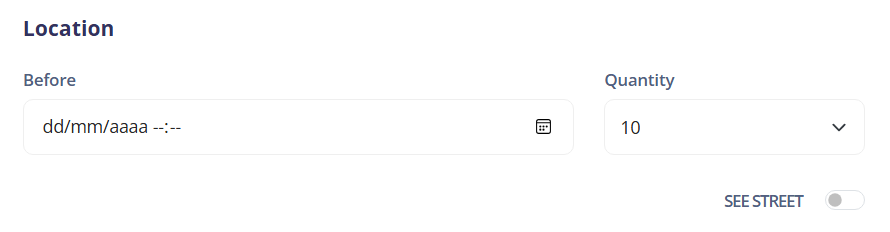
¶ History of localizations
History of localizations and link for external maps (google maps)
¶ Manage devices actions
Refers to the management actions that can be performed on devices managed by the Android Management.

-
- Reboot: Allows remotely rebooting the device. This can be useful for applying updates or resolving technical issues.
- Lock screen: Allows remotely locking the device's screen. This can be used to secure the device if it is lost or stolen.
- Clear password: Allows remotely clearing the device's screen lock password, pattern, or PIN. This can be useful if t user forgets their unlock password.
- Change password: Allows remotely changing the device's screen lock password, pattern, or PIN. This can be used enhance the security of the device.
- Status Report: Allows obtaining a report of the current status of the device, including information on setting installed apps, and compliance with policies.
- Change policy: Allows changing the management policies applied to the device. This can be used to update securi settings, app restrictions, or other policies.
- Wipe and remove: Allows wiping all data from the device and removing it from management. This is useful when a devi is lost, stolen, or no longer needed.
¶ Polices
¶ List of policies:
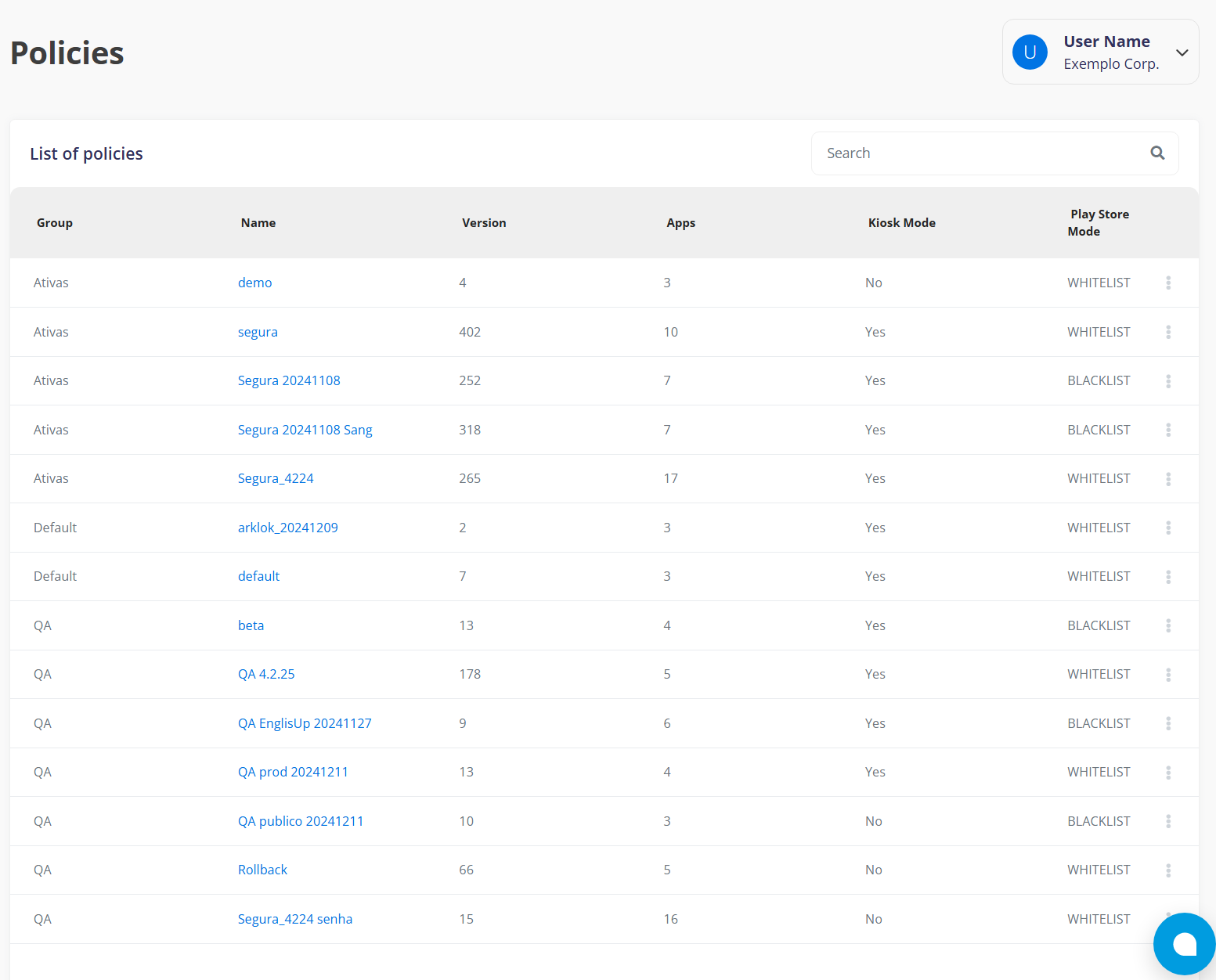
Name: Shows the name of the policy that is managing the device.
Version: Displays the automatically generated versioning number for the current version of the policy. This allows you to compare it with the policy version applied on the devices.
Apps: Lists the quantity of apps that are allowed or restricted by the policy. This can include settings for automatic app installation, app restrictions, and app permission settings.
Kiosk mode: Indicates whether kiosk mode is enabled by the policy. In kiosk mode, the device can be restricted to running only a single app or a specific set of apps.
Play Store mode: demonstrates how applications are managed.
Policy actions:
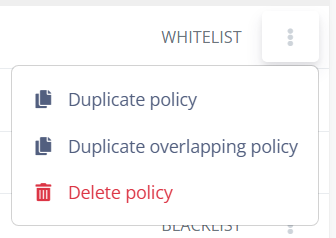
Policy override:
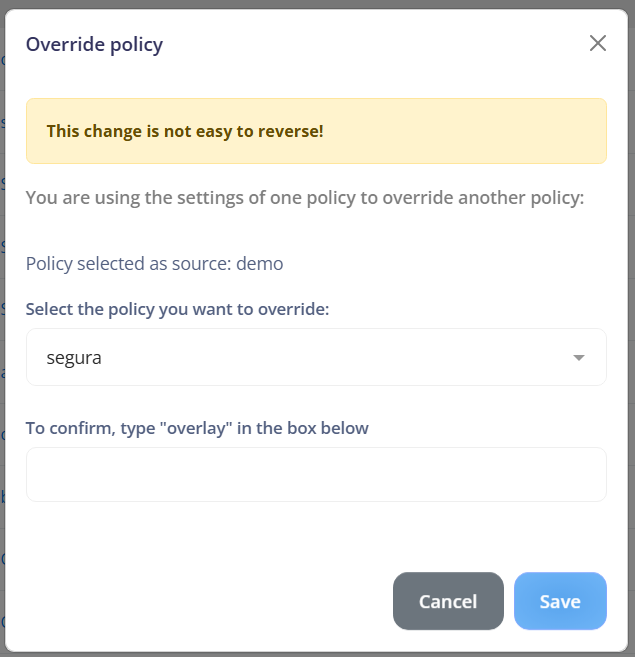
¶ Policy edit or create
¶ Policy menu
This is the policy creation or configuration menu in Nomid MDM, featuring the following sections and items:
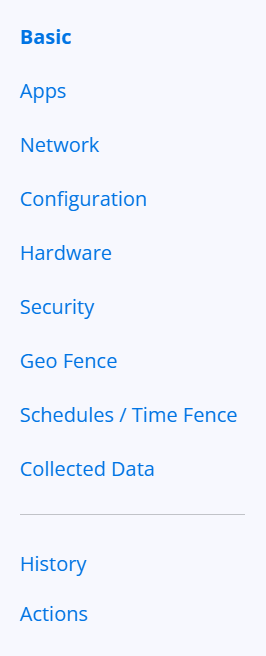
Basic: Basic settings for general policies.
Apps: Management and control of apps installed on the devices.
Network: Network settings, including Wi-Fi, VPN, and other connections.
Configuration: General configuration adjustments for the devices.
Hardware: Management of hardware components, such as camera, Bluetooth, etc.
Security: Security settings, including passwords, encryption, and permissions.
Geo Fence: Creation and management of geofences for location control.
Schedules / Time Fence: Setting schedules and timelines for policies and actions.
Collected Data: Management of data collected from devices.
History: History of actions and events related to policies.
Actions: Specific actions that can be performed on the devices, such as locking or resetting.
¶ Basic
¶ Quick setup
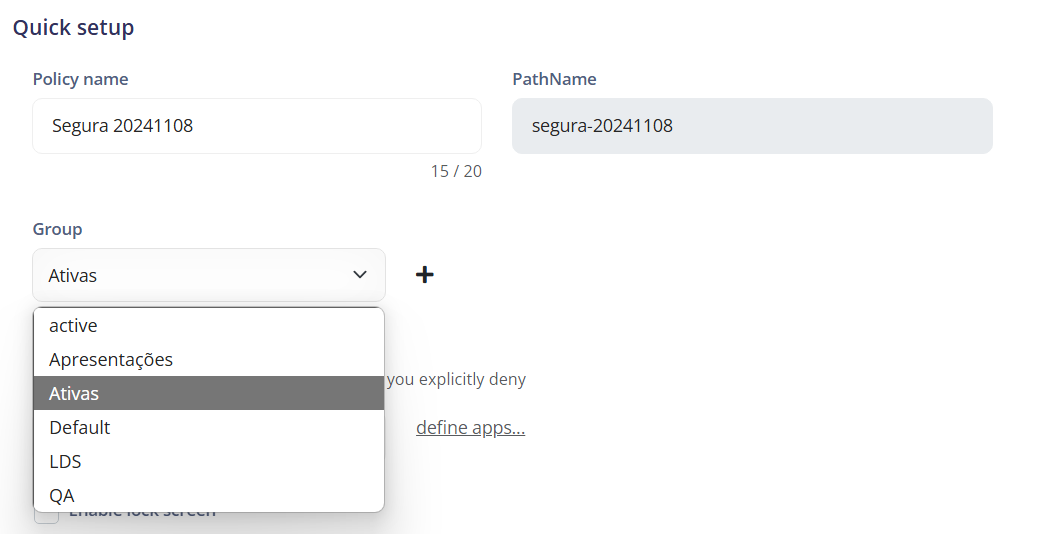
Policy name: Shows or allows editing the name of the policy.
PathName: Shows the internal id of the policy.
Policie group: Shows or allows editing the name of the group of this policy
Play Store apps mode:
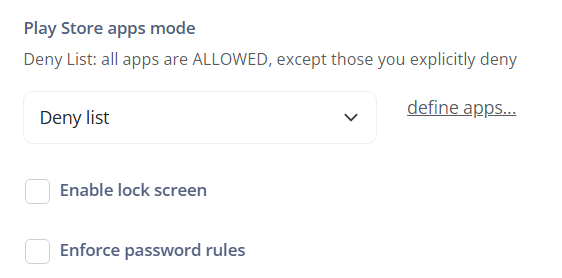
- Allow list: all apps are DENIED, except those you explicitly allow.
- Deny list: all apps are ALLOWED; except those you explicitly deny.
Define apps: Opens the configuration screen that allows you to select the applications that will be linked to the previously selected rule, whether Allow list or Deny list.
Enable lock screen: Allows enabling the screen lock on the device. This ensures that the device is protected by a PIN, pattern, or password to unlock the screen.
Enforce password rules: Allows enforcing password rules on the device. This can include requirements for password complexity, minimum length, password expiration time, and others.
System update (OTA): Refers to the settings for updating the device's operating system via Over-The-Air (OTA).
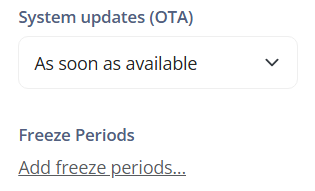
Not set: Indicates that there is no specific policy set for system updates. The device may follow the default behavior for OTA updates.
Automatic: Allows system updates to be applied automatically as soon as they are available. This ensures that the device is always up to date with the latest security patches and improvements.
Windowed: Allows setting a specific time window during which system updates are allowed. Outside of this window, updates will be postponed.
Postpone: Allows postponing system updates for a specific period. This can be useful to ensure device stability during critical periods.
Freeze Periods: Refers to specific periods during which automatic system updates are temporarily suspended to avoid disruptions at critical times.
Add freeze periods: Allows adding one or more freeze periods to the device. During these periods, automatic system updates will be postponed to ensure device stability.
Start date: Indicates the start date of the freeze period. Automatic system updates will be suspended from this date.
End date: Indicates the end date of the freeze period. Automatic system updates will resume after this date.
Wi-Fi list: Refers to the list of Wi-Fi networks configured on the device. This list can include information such as the SSID (network name), security type, and password settings for each Wi-Fi network.
Enable camera: Allows enabling or disabling the use of the camera on the device. This can be used to restrict camera access for security or privacy reasons.
Install apps enabled: Indicates whether app installation is enabled on the device. If disabled, users will not be able to install new apps, which can be useful for maintaining a controlled environment or preventing the installation of unauthorized apps.
¶ Apps
¶ App primary settings
¶ Play Store apps mode
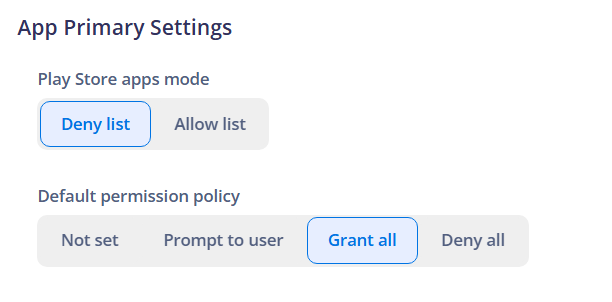
- Allow list: all apps are DENIED, except those you explicitly allow.
- Deny list: all apps are ALLOWED, except those you explicitly deny.
¶ Default permission policy
Refers to the default app permissions policy on the device. This policy determines how permissions are granted to installed apps.
- Not set: Indicates that there is no default permissions policy set. The permission granting behavior may follow the system default or be defined by other specific policies.
- Prompt to user: Means that the user will be prompted to grant or deny permissions when an app requests them. This allows the user to control the app's access to device resources and data.
- Grant all permissions: Indicates that all permissions requested by apps will be automatically granted without user intervention. This can be useful for trusted apps in controlled environments.
- Deny all permissions: Means that all permissions requested by apps will be automatically denied without user intervention. This can be used to enhance the security or privacy of the device by restricting apps' access to resources and data.
Google Play Protect verifications enforced: Indicates whether Google Play Protect verifications are being enforced on the device. Google Play Protect is a security feature that checks installed apps and device behavior to detect and prevent malware threats. When this setting is enabled, the device ensures that only secure and Google Play Protect-verified apps can be installed and run.
¶ App list
Refers to the list of apps configured to be managed on the device. This list can include information on which apps should be installed, blocked, or made available to users.
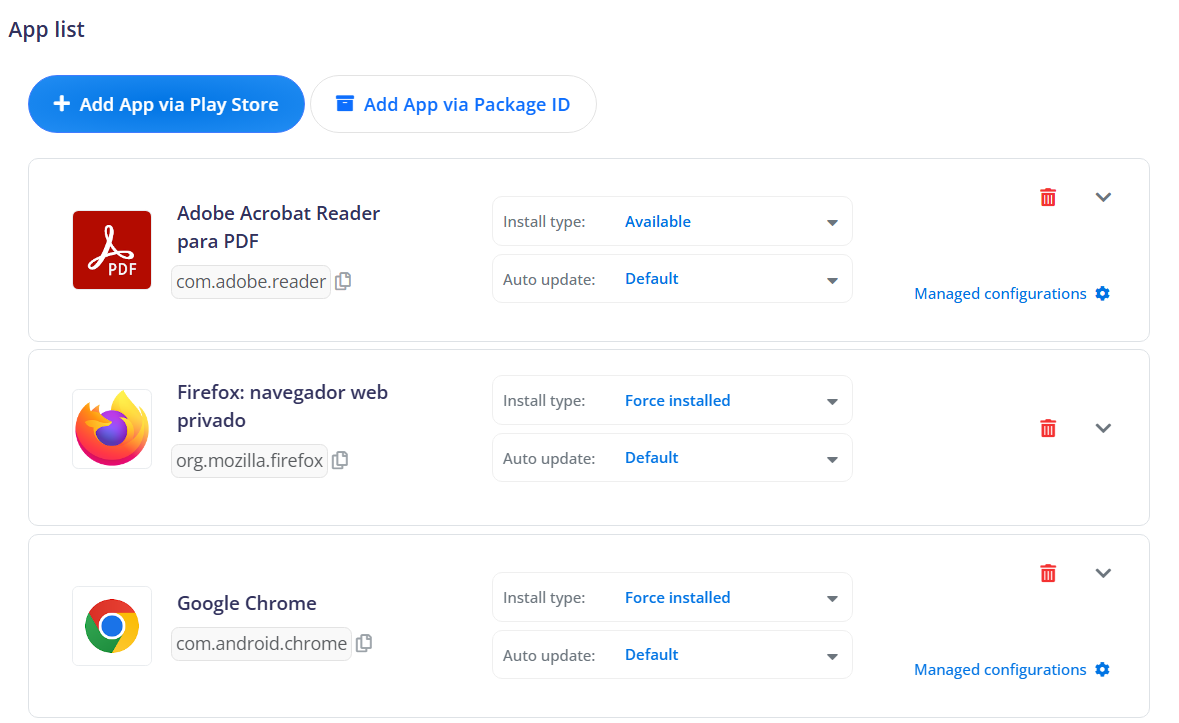
Add app: Allows adding an app to the list of managed apps. This can include specifying the app identifier (such as the package name) and other related settings.
Install type: Indicates the type of installation for the app in the managed app list. The install types can include:
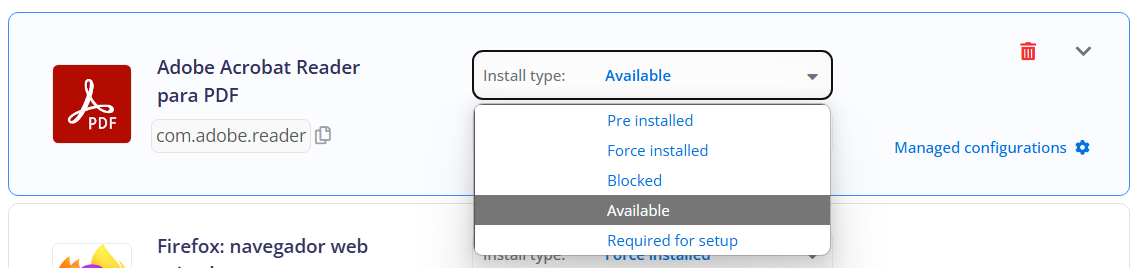
- Pre-installed: Indicates that the app is pre-installed on the device and cannot be removed by the user.
- Force installed: Means that the app is automatically installed on the device and cannot be removed by the user. This is useful for apps essential to the organization.
- Blocked: Indicates that the app is blocked and cannot be installed on the device. This is useful for preventing the installation of unwanted or unauthorized apps.
- Available: Means that the app is available for installation by the user but is not automatically installed. This allows users to choose which apps they want to install.
- Required for setup: Indicates that the app is required for the initial setup of the device and must be installed during the setup process.
Auto Update Mode:
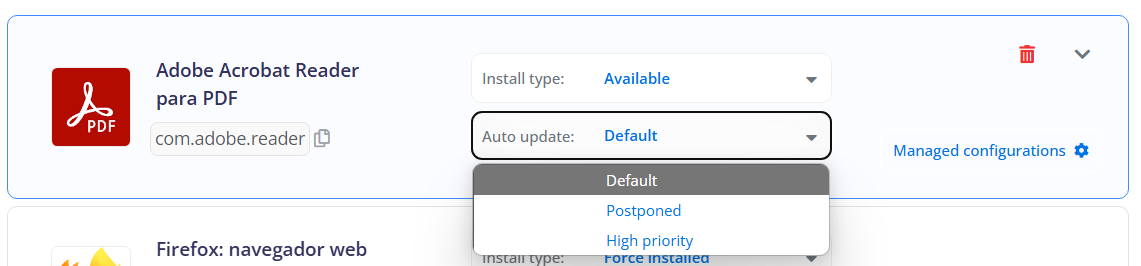
- Default: Retains the default update settings of the device.
- Postponed: Postpones the update as much as possible, usually not exceeding 30 days.
- High priority: Update as soon as possible.
¶ Advanced configuration:
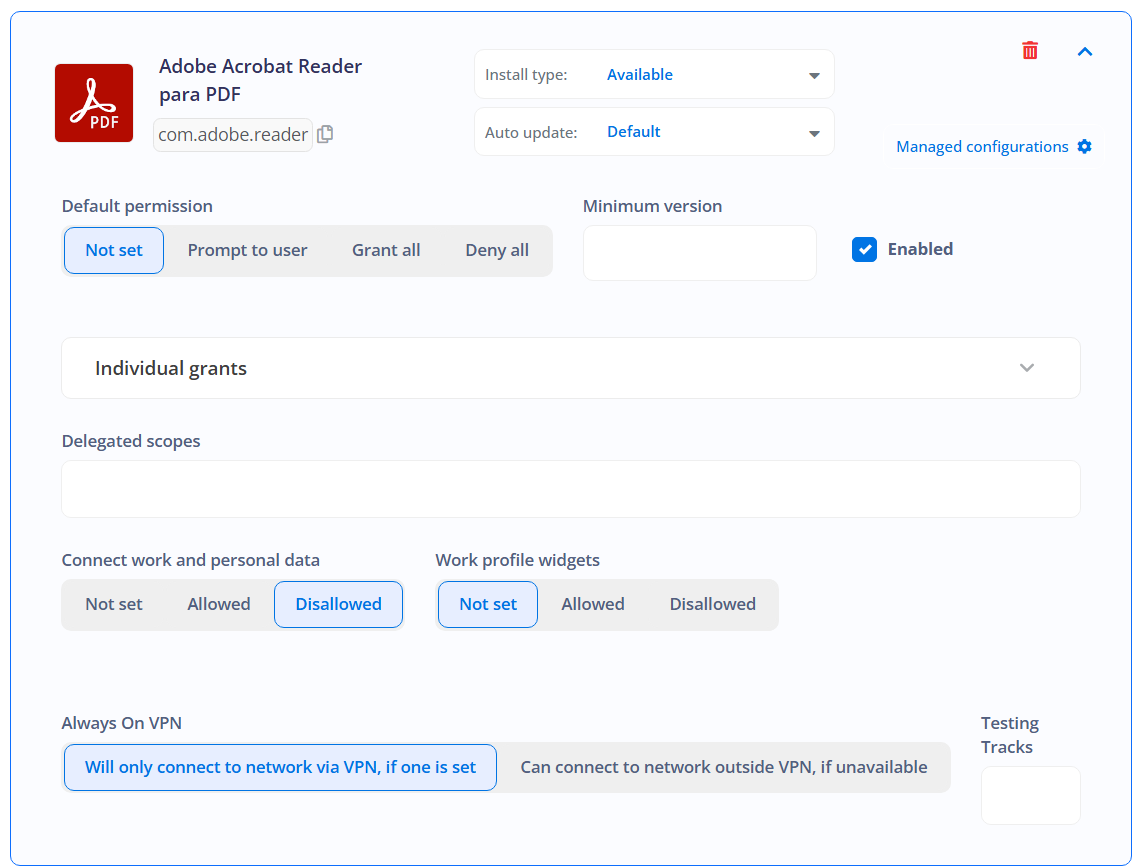
This screen allows administrators to configure installation and update settings for the applications. Key options include selecting the install type, setting auto-update priorities, granting default permissions, and specifying the minimum version for the app. Administrators can also manage individual permissions, delegated scopes, and configurations related to VPN usage, work profile widgets, and the connection of work and personal data.
¶ Managed configuration
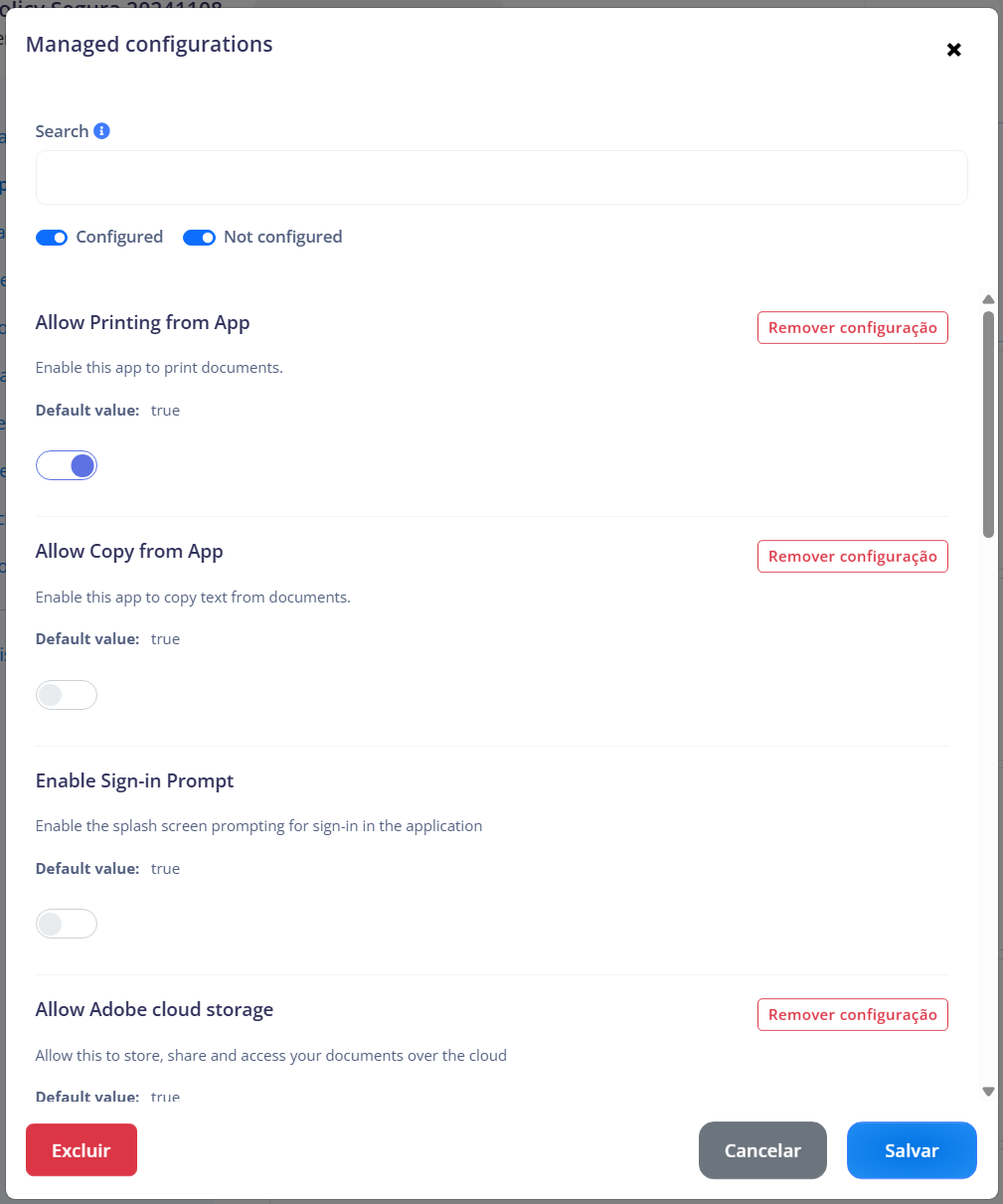
This screen allows administrators to configure various settings for the application, administrators can search for specific configurations, adjust settings as needed, and save or delete configurations using the provided buttons. Each configuration section has an option to remove specific settings if necessary.
¶ Additional Settings
Demonstrates and enables control of access to system software according to the following configuration possibilities:
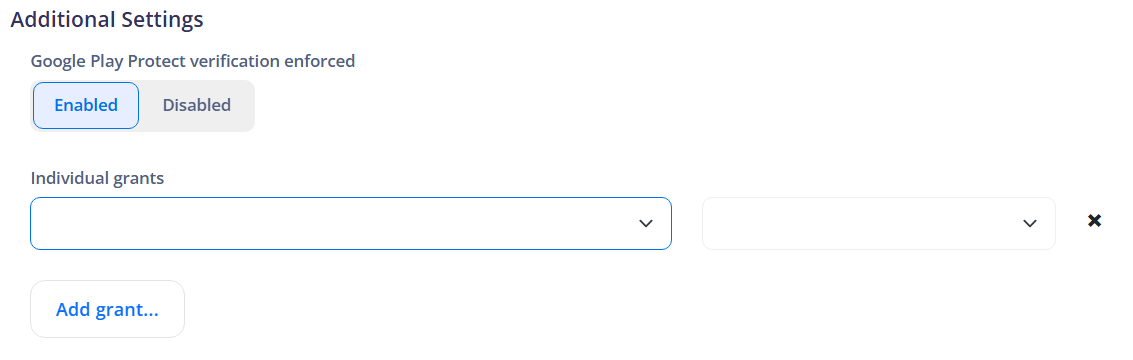
¶ Launcher (Kiosk)
Kiosk mode or Launcher, refers to the operating mode of the device in which it is restricted to running only a specific app or a limited set of apps. This is useful for devices dedicated to a single purpose or for controlled environments where access to other apps should be restricted.
You can pick from Nomid's Launcher or use an external app as the launcher app.
¶ Choose Launcher
Here, the administrator can define which application will be used as the launcher on the device. The available options are:
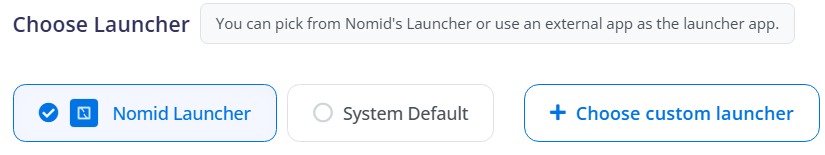
- Nomid Launcher (recommended): Provides a controlled and secure environment, allowing configuration of available apps and additional restrictions.
- System Default: Keeps the native Android launcher without Kiosk Mode restrictions.
- Choose a Custom Launcher: Allows using an external application as the launcher.
¶ Preview Launcher
The preview provides an idea of how the home screen will look within Kiosk Mode but may not exactly represent the final appearance due to variations in device screen sizes.
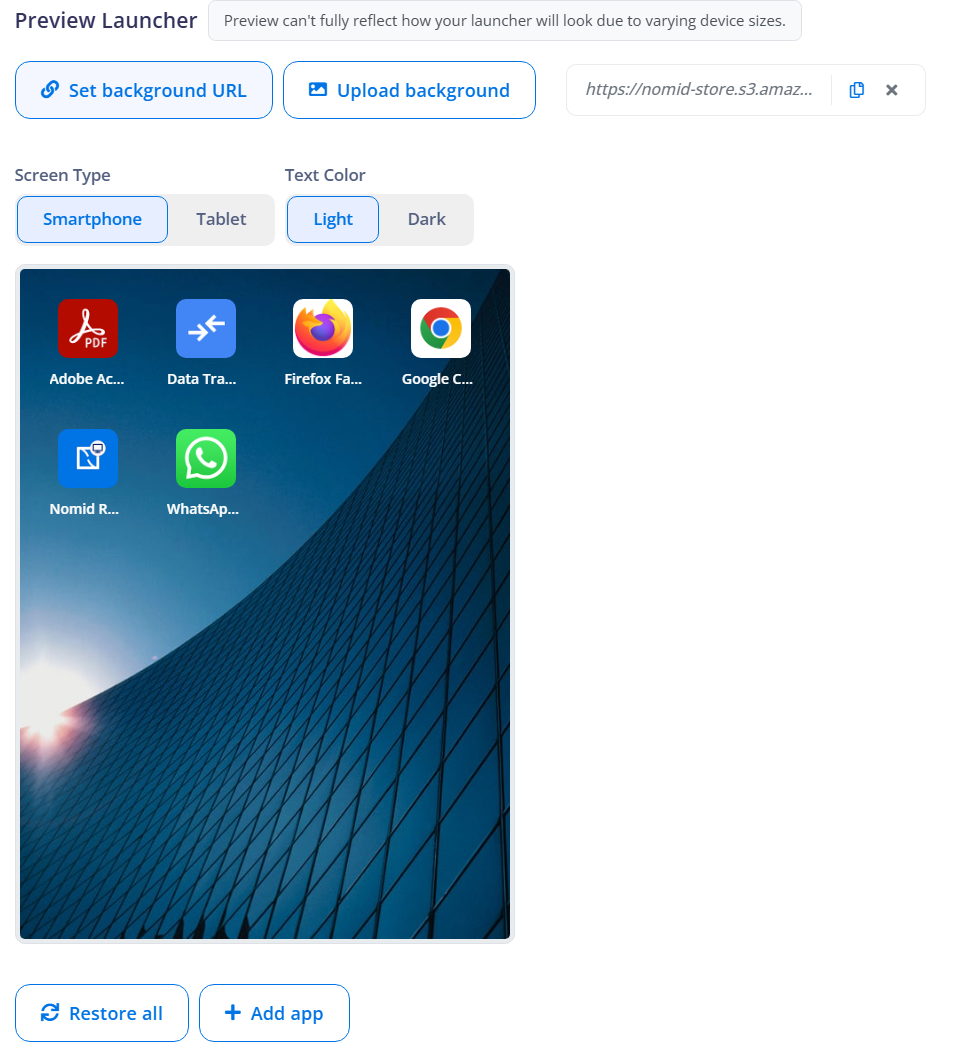
Options include:
- Change Background: Allows setting a custom image as the home screen wallpaper.
- Choose Text Color: Defines the color of the app names on the home screen, either light or dark.
- Different screen types:
- Smartphone: Displays a preview simulating a smartphone-sized screen.
- Tablet: Displays a preview simulating a tablet-sized screen.
This helps administrators understand how the interface adapts to different screen sizes.
- App Visibility Control: The preview also allows hiding specific apps from the launcher, as illustrated in the attached image. By clicking the X icon on an app, it can be removed from the visible interface, ensuring only authorized applications remain accessible.
¶ Define App Visibility Based on Their Source
This setting allows selecting which apps will be visible in the launcher based on their source:
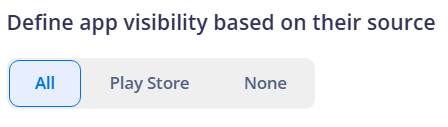
- All: All allowed apps will be displayed.
- Play Store Only: Only apps installed via Google Play will be shown.
- None: No apps will be displayed that are not managed by the policy.
¶ Additional Settings
Nomid MDM provides various advanced settings for even stricter control over the device:
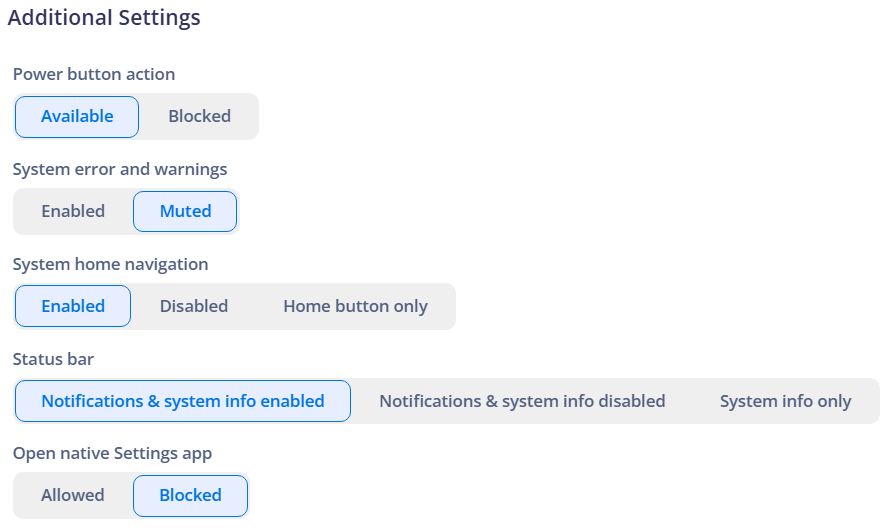
¶ Power Button Action
- Available: The power button can be used normally.
- Blocked: Prevents the use of the power button, avoiding unauthorized shutdown or restart.
¶ System Error and Warning Messages
- Enabled: The device displays system error messages and warnings.
- Muted: Blocks error notifications and system messages to prevent distractions or unnecessary interactions.
¶ System Home Navigation
- Enabled: Maintains the standard Android navigation.
- Disabled: Completely hides the navigation bar, preventing users from accessing other system areas.
- Home Button Only: Keeps only the "Home" button, limiting navigation to a single screen.
¶ Status Bar
- Notifications & System Info Enabled: Allows notifications and system information to be displayed in the status bar.
- Disabled: Completely hides the status bar.
- System Info Only: Hides notifications but keeps basic information such as time and battery status.
¶ Access to the Settings App
- Allowed: The user can access system settings.
- Blocked: Access to Android settings is restricted, preventing unauthorized modifications.
¶ Network
Refers to the network settings and policies that can be applied to devices to manage access to Wi-Fi networks, mobile networks, Bluetooth, and VPN.
¶ Manage Network
Indicates the network management actions that can be performed on devices.
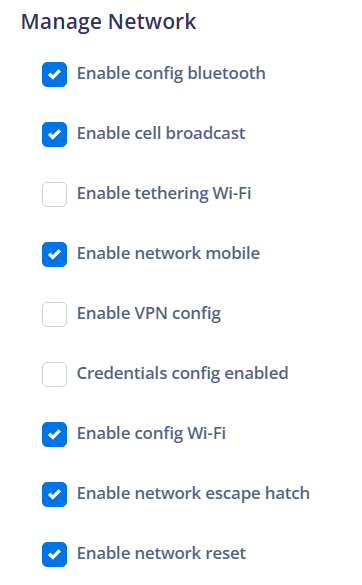
Enable config Bluetooth: Allows enabling or disabling Bluetooth configuration on the device. This can be used to control Bluetooth usage for security or power-saving reasons.
Enable cell broadcast: Allows enabling or disabling cell broadcast messaging on the device. This is used to receive emergency alerts and other cell broadcast messages.
Enable tethering Wi-Fi: Allows enabling or disabling Wi-Fi tethering on the device. This allows the device to share its internet connection with other devices.
Enable network mobile: Allows enabling or disabling mobile network access on the device. This controls the device's ability to connect to mobile data networks.
Enable VPN config: Allows enabling or disabling VPN configuration on the device. This allows the device to establish secure virtual private network connections.
Credentials config enabled: Allows enabling or disabling credentials configuration on the device. This includes the installation and management of digital certificates and other security credentials.
Enable config Wi-Fi: Allows enabling or disabling Wi-Fi configuration on the device. This controls the device's ability to connect to Wi-Fi networks.
Enable network escape hatch: Allows enabling or disabling the network escape hatch mechanism on the device. This allows the device to temporarily connect to an unmanaged network in emergency situations to retrieve management policies or updates.
Enable network reset: Allows enabling or disabling the ability to reset network settings on the device. This can be used to restore default network settings in case of connectivity issues.
¶ Manage VPN Always-On
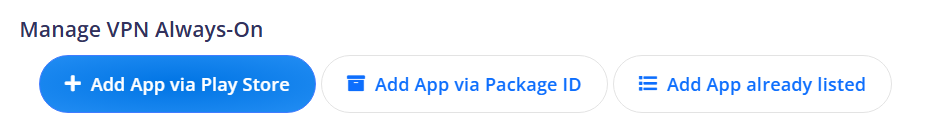
Indicates the ability to manage the Always-On VPN configuration on devices. Always-On VPN maintains a constant VPN connection, ensuring that all device network traffic is routed through the VPN.
Add app: Allows adding an app to the list of apps that can utilize the Always-On VPN connection. This is useful for ensuring that specific apps always connect securely through the VPN:
- Add pachage;
- Add playstore;
- Add app already listed.
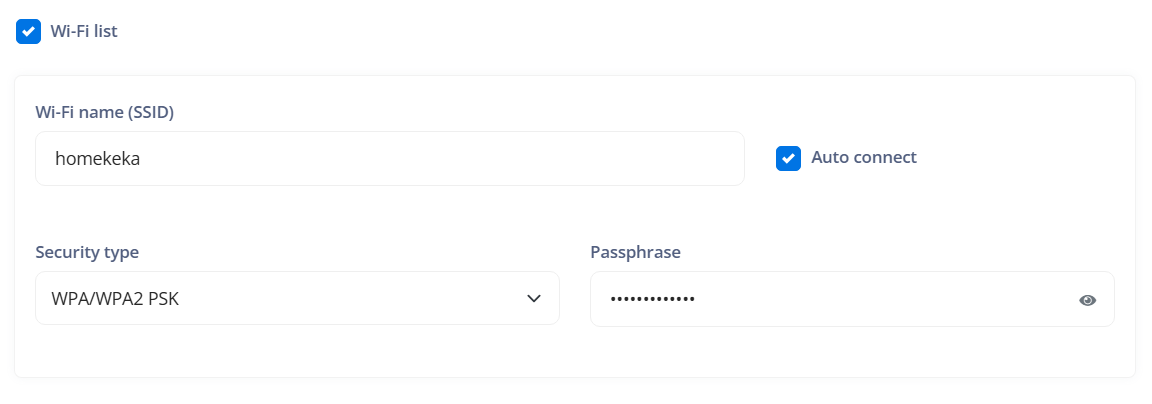
¶ Setup default Wi-Fi
Indicates the ability to configure a default Wi-Fi network on devices. This can include adding details of the Wi-Fi network such as the name (SSID), security type, and auto-connect settings.
Add Wi-Fi network: Allows adding a new Wi-Fi network to the device's configuration.
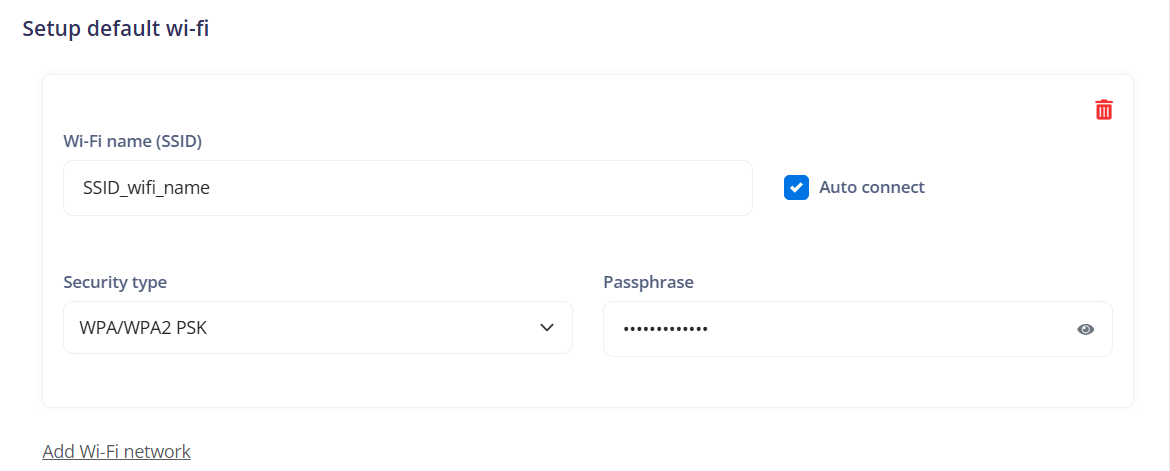
Wi-Fi name (SSID): Refers to the name of the Wi-Fi network (Service Set Identifier) that the device should connect to.
Auto connect: Indicates whether the device should automatically connect to this Wi-Fi network when it is in range.
Security type: Specifies the type of security used by the Wi-Fi network. This can include:
None: Indicates that the Wi-Fi network has no security and is open for connection.
WEP: Refers to Wired Equivalent Privacy, an older and less secure type of security for Wi-Fi networks.
WPA/WPA2 PSK: Indicates Wi-Fi Protected Access or Wi-Fi Protected Access 2 with a pre-shared key, which are more modern and secure methods of security for Wi-Fi networks.
¶ Recommended global proxy
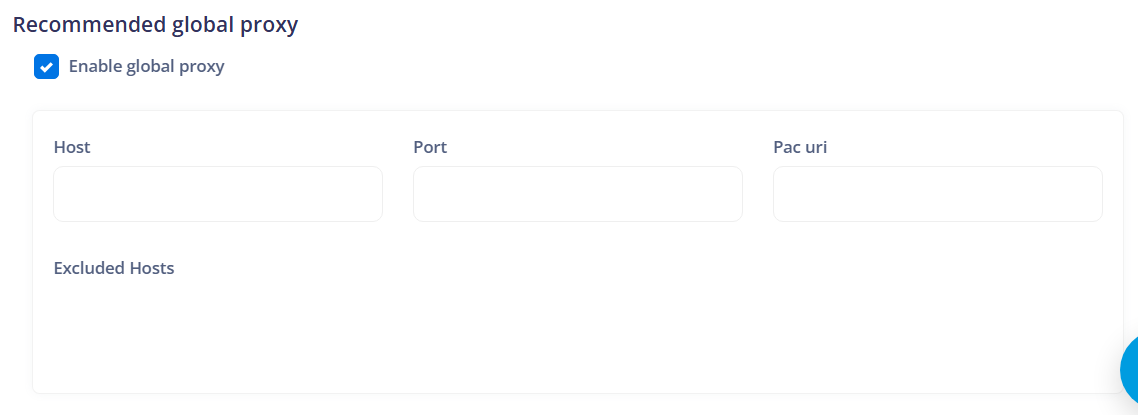
Suggests configuring a global proxy for the device. This can be useful for routing all network traffic from the device through a proxy server for security or monitoring purposes.
Enable global proxy: Allows enabling or disabling the use of a global proxy on the device. If enabled, all network traffic from the device will be routed through the specified proxy server.
¶ Configuration
Refers to the general device settings that can be managed to control specific features and behaviors of the device.
¶ Manage Configuration
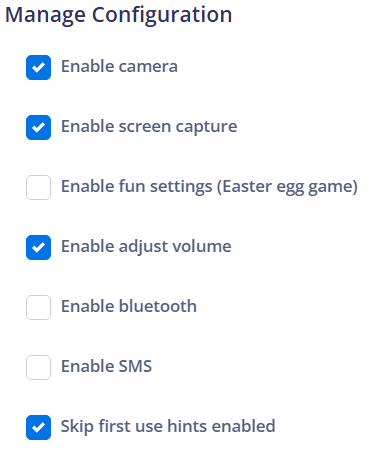
Indicates the ability to manage various device settings to customize its functionality and security.
Enable camera: Allows enabling or disabling the use of the camera on the device. This can be used to restrict camera access for security or privacy reasons.
Enable screen capture: Allows enabling or disabling the ability to capture the device's screen. This can be used to prevent unauthorized sharing of sensitive information.
Enable fun settings (Easter egg game): Allows enabling or disabling fun settings, such as the hidden Easter egg game in the Android system settings. This is typically used for entertainment purposes.
Enable adjust volume: Allows enabling or disabling the ability to adjust the volume of the device. This can be used to control the volume level in specific environments.
Enable bluetooth: Allows enabling or disabling the use of Bluetooth on the device. This can be used to control Bluetooth connectivity for security or power-saving reasons.
Enable SMS: Allows enabling or disabling the sending and receiving of SMS messages on the device. This can be used to restrict SMS communication on corporate devices.
Skip first use hints enabled: Allows enabling or disabling the display of first-use hints on the device. This can be used to streamline the initial setup experience for end-users.
¶ Policy configuration
Indicates the ability to configure management policies for the device, which may include app permissions, system updates, and user settings.
¶ Default permission policy
Refers to the default app permissions policy on the device. This policy determines how permissions are granted to installed apps.
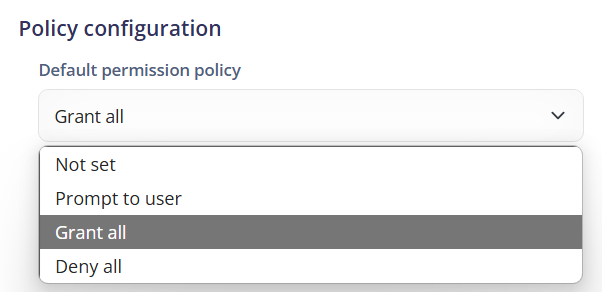
- Not set: Indicates that there is no default permissions policy set. The permission granting behavior may follow the system default or be defined by other specific policies.
- Prompt to user: Means that the user will be prompted to grant or deny permissions when an app requests them. This allows the user to control the app's access to device resources and data.
- Grant all permissions: Indicates that all permissions requested by apps will be automatically granted without user intervention. This can be useful for trusted apps in controlled environments.
- Deny all permissions: Means that all permissions requested by apps will be automatically denied without user intervention. This can be used to enhance the security or privacy of the device by restricting apps' access to resources and data.
Enable create window: Allows enabling or disabling the ability for apps to create overlay windows on the screen. This can be used to control the display of overlay content for security or user experience reasons.
Enable keyguard: Allows enabling or disabling the keyguard, which is the device's lock screen. This can be used to control access to the device when it is locked.
Keyguard features can be disabled: Indicates which keyguard (lock screen) features can be disabled, such as notifications, camera, or quick response.
Enable lock screen: Allows enabling or disabling the screen lock on the device. This ensures that the device is protected by a PIN, pattern, or password to unlock the screen.
System updates (OTA): Refers to the settings for updating the device's operating system via Over-The-Air (OTA).
- Not set: Indicates that there is no specific policy set for system updates. The device may follow the default behavior for OTA updates.
- Automatic: Allows system updates to be applied automatically as soon as they are available. This ensures that the device is always up to date with the latest security patches and improvements.
- Windowed: Allows setting a specific time window during which system updates are allowed. Outside of this window, updates will be postponed.
- Postpone: Allows postponing system updates for a specific period. This can be useful to ensure device stability during critical periods.
Freeze Periods: Refers to specific periods during which automatic system updates are temporarily suspended to avoid disruptions at critical times.
Add freeze periods: Allows adding one or more freeze periods to the device. During these periods, automatic system updates will be postponed to ensure device stability.
- Start date: Indicates the start date of the freeze period. Automatic system updates will be suspended from this date.
- End date: Indicates the end date of the freeze period. Automatic system updates will resume after this date.
Settings to user: Refers to the settings related to user management on the device.
Add user enabled: Allows enabling or disabling the ability to add new users to the device. This can be used to control access to the device by multiple users.
Remove user enabled: Allows enabling or disabling the ability to remove users from the device. This can be useful for managing access to the device in corporate environments.
Set user icon enabled: Allows enabling or disabling the ability to set custom icons for users on the device. This can be used to personalize the user experience.
Set wallpaper enabled: Allows enabling or disabling the ability to set custom wallpapers on the device. This can be used to personalize the appearance of the device.
¶ Hardware
Refers to the settings and policies related to the device's hardware that can be managed to control access to physical features and security options.
¶ [Manage] Hardware
Indicates the ability to manage the hardware settings of the device.
Enable factory reset: Allows enabling or disabling the ability to perform a factory reset on the device. This can be used to control the security of the device by preventing unwanted resets.
Enable safe boot: Allows enabling or disabling the ability to boot the device in safe mode. Safe mode can be used to troubleshoot the device by disabling third-party apps.
Enable mount physical media: Allows enabling or disabling the ability to mount physical media, such as USB drives or SD cards, on the device. This can be used to control access to external data.
Debugging features allowed: Indicates whether debugging features, such as USB Debugging, are allowed on the device. This can be used to control access to development and debugging tools.
Modify account enabled: Allows enabling or disabling the ability to modify accounts on the device. This can be used to control the management of user accounts and data synchronization.
Enable unmute microphone: Allows enabling or disabling the ability to unmute the microphone on the device. This can be used to control access to the microphone for privacy or security reasons.
¶ Battery mode
Indicates the settings related to the battery management of the device.
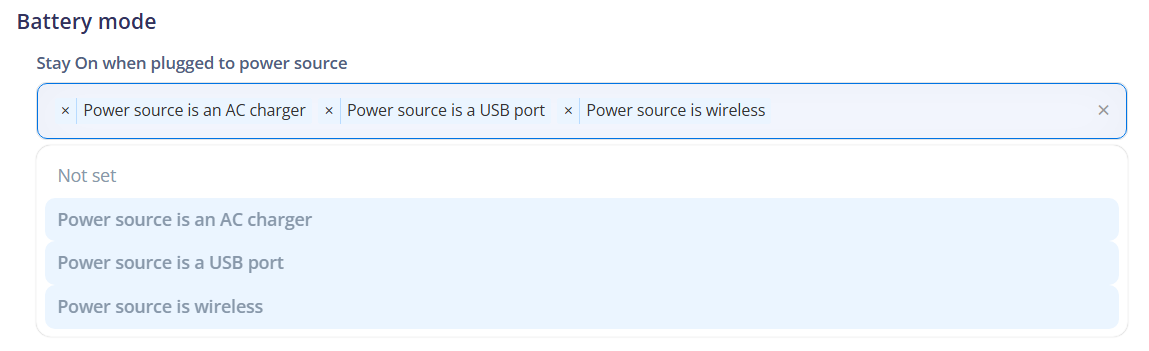
- Stay on plugged modes: Refers to the settings that determine the behavior of the device when it is connected to a power source.
- Not set: Indicates that there is no specific setting defined for the behavior of the device when connected to a power source. The device may follow the system's default behavior.
- Power source is an AC charger: Indicates that the device should stay on when connected to an alternating current (AC) charger.
- Power source is a USB port: Indicates that the device should stay on when connected to a USB port.
- Power source is wireless: Indicates that the device should stay on when connected to a wireless power source.
¶ Security
Refers to the settings and policies related to the security of the device that can be managed to protect the data and access to the device.
¶ Manage security
Indicates the ability to manage the security settings of the device.
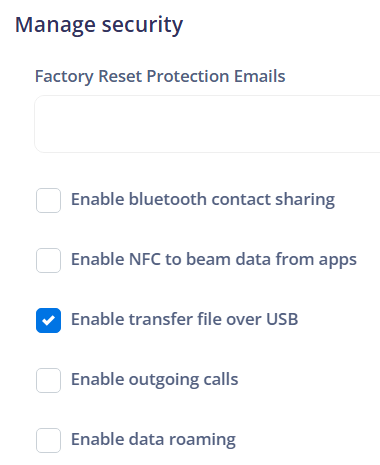
"Factory reset protection emails": Refers to the email addresses that are notified in case of a factory reset of the device. This can be used as a security measure to alert administrators about unauthorized factory resets.
Enable Bluetooth contact sharing: Allows enabling or disabling the ability to share contacts via Bluetooth. This can be used to control the exchange of personal information through Bluetooth.
Enable NFC to beam data from apps: Allows enabling or disabling the ability to beam data from apps via Near Field Communication (NFC). This can be used to control the exchange of data through NFC.
Enable transfer file over USB: Allows enabling or disabling the ability to transfer files between the device and a computer via USB. This can be used to control access to the device's data through USB connections.
Enable outgoing calls: Allows enabling or disabling the ability to make outgoing calls on the device. This can be used to control the use of the device for voice communications.
Enable data roaming: Allows enabling or disabling data roaming on the device. This can be used to control the use of mobile data when the device is outside the main mobile network coverage area.
Auto-update policy: Refers to the policy for automatic app updates on the device. This policy determines how and when apps are automatically updated.
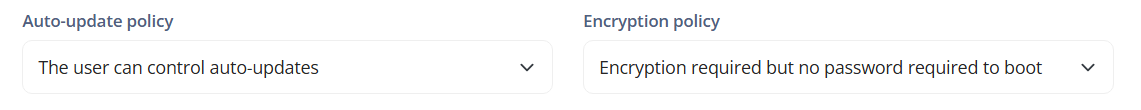
- The user can control auto-updates: Indicates that the user has the ability to control the auto-update settings for apps. The user can choose to turn auto-updates on or off as desired.
- Apps are auto updated at any time. Data charges may apply: Indicates that apps are automatically updated at any time, regardless of the type of data connection. This may result in data charges if the update occurs while the device is using mobile data.
- Apps are auto updated over Wi-Fi only: Indicates that apps are automatically updated only when the device is connected to a Wi-Fi network. This prevents the use of mobile data for app updates.
- Apps are never auto updated: Indicates that apps are not automatically updated. The user must manually update the apps as needed.
Encryption policy: Refers to the device's encryption policy. This policy determines the encryption requirements to protect the data stored on the device.
- Encryption not required: Indicates that encryption is not required for the device. Data can be stored on the device without encryption.
- Encryption required but no password required to boot: Indicates that encryption is required to protect the data stored on the device, but no password is required to boot the device.
- Encryption required with password required to boot: Indicates that encryption is required to protect the data stored on the device, and a password is required to boot the device. This provides an additional level of security.
¶ Location
Refers to the settings related to the management of the device's location.
Enable share location: Allows enabling or disabling the device's ability to share its location. This can be used to control access to location information by apps and services.
Location mode: Determines the operation mode of the device's location settings.
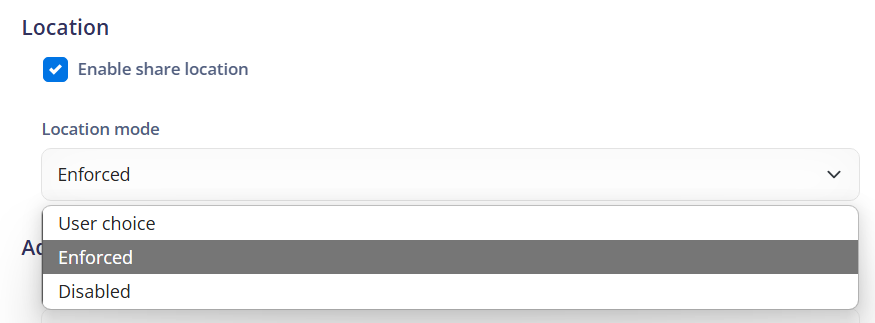
- User choice: Allows the user to choose the location settings. The user can turn location services on or off as desired.
- Enforced: Enforces the use of location services. The device will always share its location, and the user cannot turn off location services.
- Disabled: Completely disables location services. The device will not share its location, and the user cannot turn on location services.
¶ Advanced security overrides
Refers to the settings that allow the override of advanced security policies on the device.
Untrusted apps policy: Determines the policy for the installation of untrusted apps (also known as apps from unknown sources) on the device.
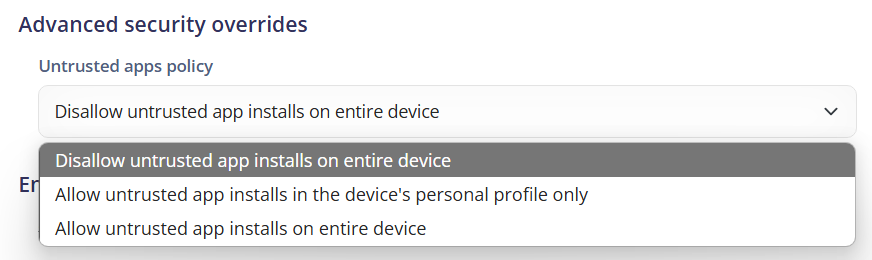
- Disallow untrusted app installs on entire device: Prevents the installation of untrusted apps on the entire device. This enhances security by restricting installations to apps from trusted sources, such as the Google Play Store.
- Allow untrusted app installs in the device's personal profile only: Allows the installation of untrusted apps only in the device's personal profile, while prohibiting such installations in other profiles or the work profile. This provides a balance between security and flexibility.
- Allow untrusted app install on entire device: Allows the installation of untrusted apps on the entire device. This offers greater flexibility but may increase security risk.
¶ Enforcement Rules
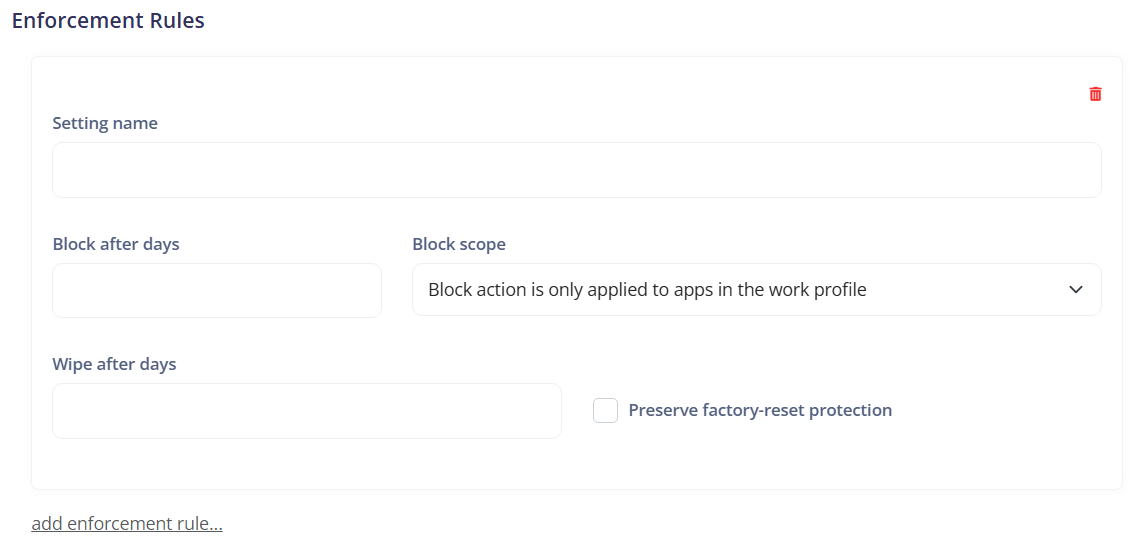
Refers to the rules that can be set to enforce security policies on the device.
Add enforcement rule: Allows adding a new enforcement rule to enforce a specific security policy.
Setting name: Refers to the name of the setting or policy being enforced by the enforcement rule.
Block after days: Specifies the number of days after which the block action will be applied if the policy is not complied with.
Block scope:
- Not set: Indicates that the block scope is not defined. The default behavior may be applied.
- Block action is only applied to apps in the work profile: Indicates that the block action will be applied only to apps within the work profile.
- Block actions is applied to the entire device, including apps in the personal profile: Indicates that the block action will be applied to the entire device, including apps in the personal profile.
Wipe after days: Specifies the number of days after which the device will be wiped (reset to factory settings) if the policy is not complied with.
Preserve factory-reset protection: Indicates whether the factory-reset protection should be preserved after the device is wiped. This can be used to maintain the security of the device even after it is wiped.
¶ Password requirements
Refers to the password policies that can be set to ensure the security of the device.
Add new password requirements: Allows adding new password requirements for the device.
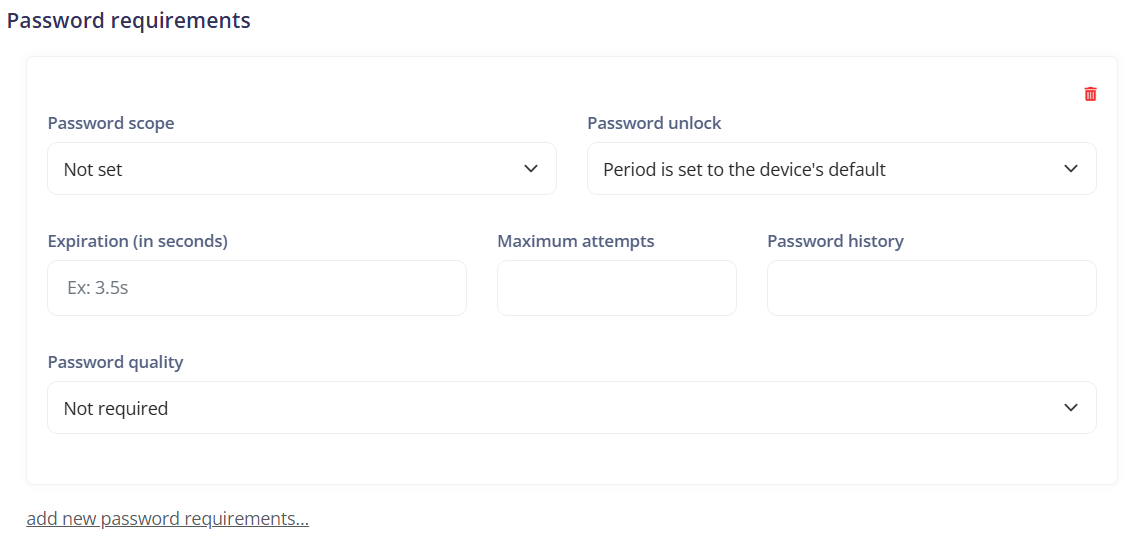
Password scope:
- Not set: Indicates that the password scope is not defined. The default behavior of the device may be applied.
- Only applied to the device: Indicates that the password requirements are applied to the entire device.
- Only applied to the work profile: Indicates that the password requirements are applied only to the work profile of the device.
Password unlock:
- Period is set to the device's default: Indicates that the password unlock period is set to the device's default. The user must enter the password after the inactivity period defined by the device.
- Period is set to 24 hours: Indicates that the user must enter the password to unlock the device at least once every 24 hours.
Expiration (in seconds): Specifies the period of time, in seconds, after which the device's password expires and the user must set a new password.
Maximum attempts: Sets the maximum number of incorrect password attempts allowed before the device is locked or wiped.
Password history: Specifies the number of unique recent passwords that the device remembers to prevent the user from reusing old passwords.
Password quality: Defines the level of complexity required for the device's password. It may include requirements such as the presence of letters, numbers, and special characters.
¶ Choose private key rule
Refers to the settings that allow the selection of private keys for use in authentication and other security operations.
Private key selection enabled: Allows enabling or disabling the ability to select private keys on the device. This can be used to control access to private keys for security operations.
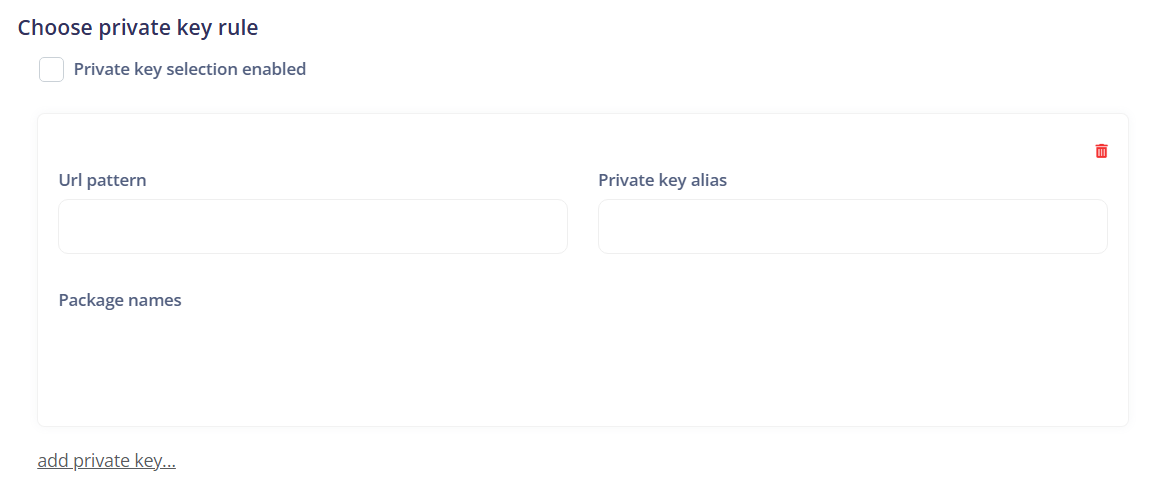
Add private key: Allows adding a new private key to the device for use in authentication and other security operations.
Url pattern: Specifies the URL pattern for which the private key will be used. This can be used to restrict the use of private keys to certain websites or services.
Private key alias: Refers to the name or alias associated with the private key. This is used to identify the private key on the device.
Package names: Specifies the names of application packages that are allowed to use the private key. This can be used to restrict access to the private key to specific apps.
¶ Permitted accessibility services
Refers to the settings that determine which accessibility services can be used on the device. Accessibility services are features designed to help users with disabilities interact with the device.
Package names: Specifies the names of application packages that are allowed to use accessibility services on the device. This can be used to restrict access to accessibility services to specific apps.
¶ Geo Fence:
Refers to the settings and policies related to the delineation of a specific geographical area for the device. The geofence can be used to restrict the device's use to a defined area or to send notifications when the device enters or exits that area.
¶ [Manage] Geo Fence
Indicates the ability to manage the geofence settings for the device.
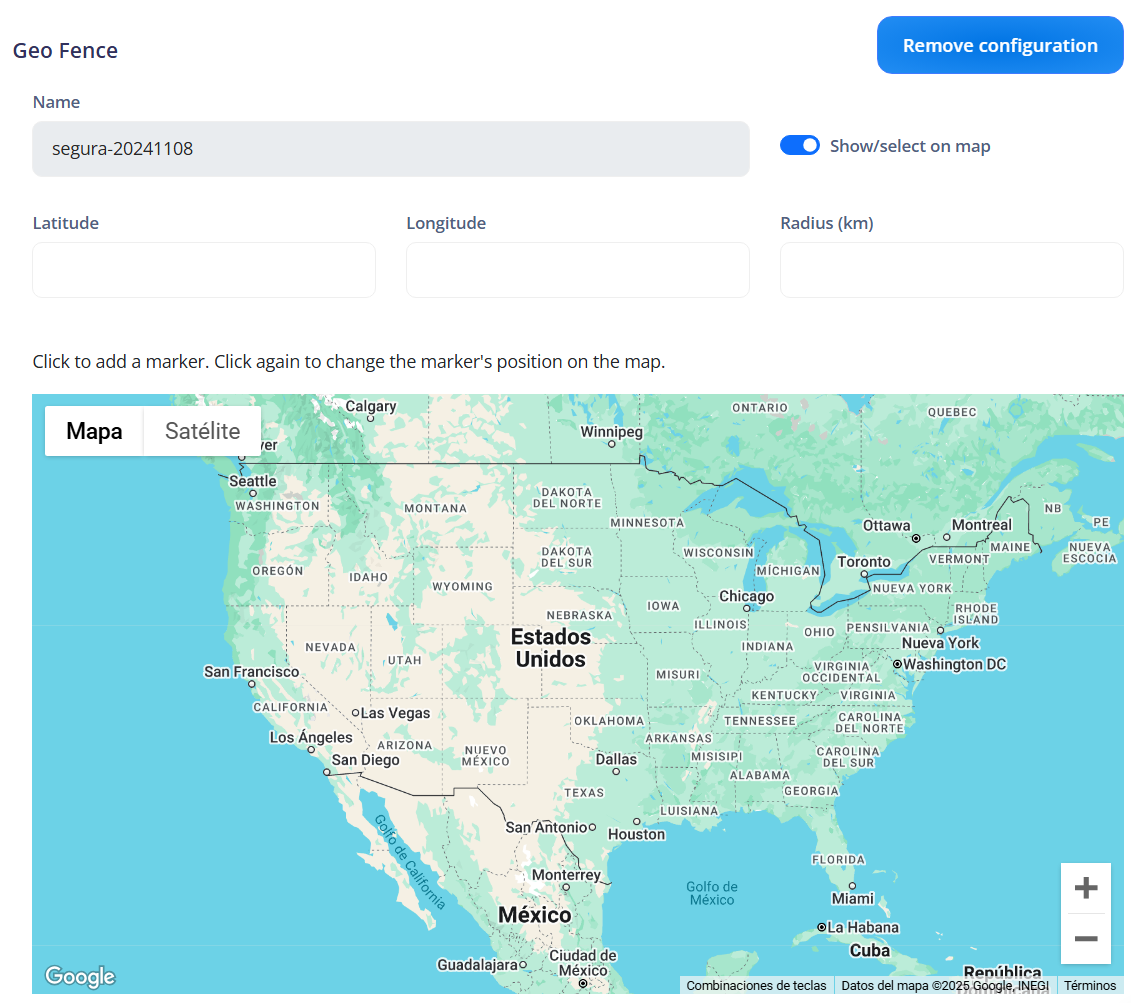
Name: Refers to the name of the geofence. This is used to identify the geofence on the device.
Show/select on map: Allows showing and selecting the geofence area on a map. This can be used to visually define the location and boundaries of the geofence.
Latitude, Longitude and Radius (km): Specifies the geographical coordinates (latitude and longitude) of the center of the geofence and the radius of the area in kilometers. This defines the boundaries of the geofence.
Violation notification: Refers to the setting that determines whether a notification will be sent when the device enters or exits the area defined by the geofence. This can be used to alert administrators or users about violations of the geographical boundaries.
¶ Schedules / Time Fence
Refers to the settings related to managing the device's usage time. This can include setting working hours and restricting access to work apps outside of those hours.
¶ [Manage] Schedules / Time Fence
Indicates the ability to manage the schedules and time fence settings for the device.
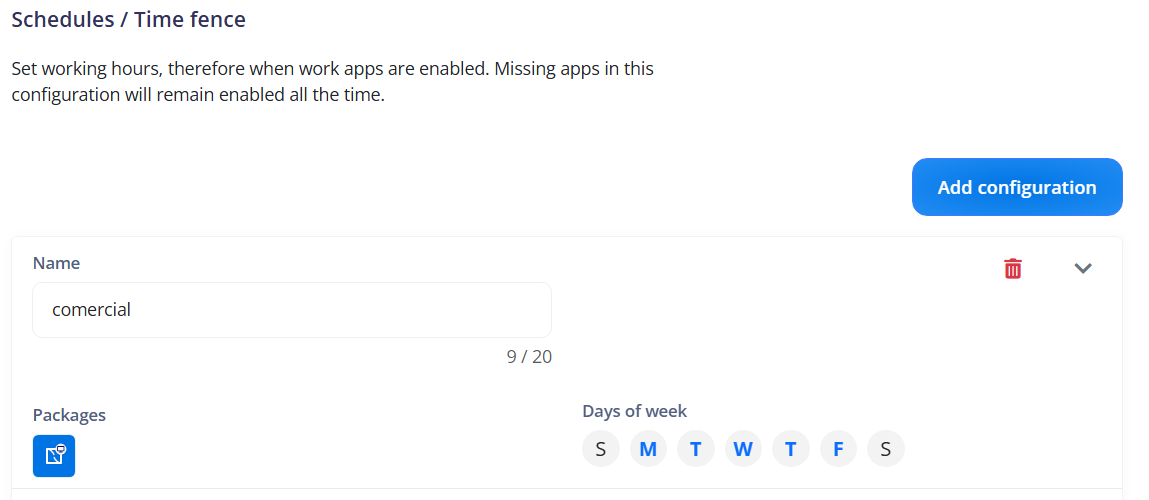
Set working hours, and therefore when work apps are enabled: Allows setting the working hours during which work apps are enabled on the device. Outside of these hours, access to work apps may be restricted.
Name: Refers to the name of the schedule or time fence. This is used to identify the setting on the device.
Default rule: Specifies the default rule that will be applied when the device is outside the defined working hours. This can include disabling work apps or restricting access to certain features.
Packages: Lists the package names of the apps that are affected by the schedule or time fence. This can be used to specify which work apps are enabled or restricted based on working hours.
¶ Days of week
Specifies the days of the week on which the schedule or time fence is active. This can be used to apply different time rules for weekdays and weekends, for example.
¶ Report
Refers to the reports generated about the device, which can include information about apps, device settings, hardware information, network, and more.
¶ [Manage] Device report
Indicates the ability to manage and view reports about the device.
Apps report level: Defines the level of detail included in the report about the apps installed on the device.
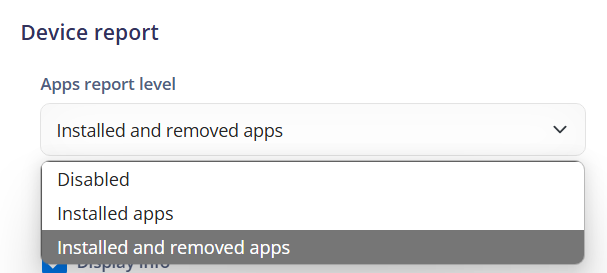
Disabled: Indicates that the app report is disabled and will not include information about installed apps.
Installed apps: Indicates that the report will include information only about the apps currently installed on the device.
Installed and removed apps: Indicates that the report will include information about the apps installed and also about the apps that have been removed from the device.
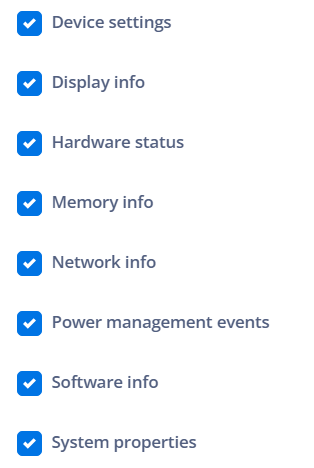
Device settings: Includes information about the current settings of the device in the report.
Display info: Includes information about the device's display, such as resolution and pixel density.
Hardware status: Includes information about the hardware status of the device, such as battery and CPU usage.
Memory info: Includes information about the device's memory, such as total memory and available memory.
Network info: Includes information about the device's network, such as Wi-Fi connection status and mobile data.
Power management events: Includes information about events related to the device's power management, such as power-saving mode and shutdowns.
Software info: Includes information about the device's software, such as operating system version and security updates.
System properties: Includes information about the system properties of the device, such as system settings and hardware properties.
¶ History
Refers to the record of changes to the device's settings and policies over time. This can include previous versions of the policies, who made the changes, and when they were made.
¶ [Manage] History
Indicates the ability to manage and view the history of changes to the device's settings and policies.
History table: Displays a table that records the changes made to the device's settings and policies.
Version: Refers to the version of the policy or setting. This can be used to identify different iterations of the policies over time.
User: Indicates the user or administrator who made the change to the policy or setting.
Date: Specifies the date and time when the change was made.
¶ Actions
View policy: Allows viewing the details of the policy or setting for that specific version.
Restore policy: Allows restoring the policy or setting to that specific version, reverting the device to the settings of that version.
¶ Actions for policy
¶ Copy policy
Allows you to create a new policy based on the current policy or overlay another policy with the current policy settings.
Selected policy: displays name of the policy selected to be duplicated.
Existing policy: Allows you to replace existing policy settings with the selected policy settings.
Name of the new policy: Depending on the Existing policy configuration, it allows you to name the new policy created by the duplication or select the policy that will have the settings replaced.
¶ Delete Policy
Deletes the selected policy after confirming the deletion request. Please note that this is a non-return action after confirmation.
¶ Company
¶ Summary
Legal name:
Trade name:
Google enterprise Id:
¶ Users
¶ Users table
User:
Email:
¶ Actions
¶ Edit
User:
Edit username.
Permissions:
- View device list:
- View device location:
- View device detail:
- View policy:
- View company users:
- View policy time fence:
- View company billing:
- View company integrations:
- View policy Geo Fence:
- View policy history:
- View company:
- View policy list:
- Edit policy:
- Edit Zero Touch:
- Edit company billing:
- Edit company integrations:
- Edit company users:
- Edit device tags:
- Send command to device:
- Enroll policy:
Policies:
Policies that the user has access to, both the configuration (if allowed) and the devices contained.
¶ Sent email with password
¶ Disable from company
¶ Enrollment
¶ New policy
The policy creation and configuration screens in Nomid MDM offer an intuitive interface for administrators to create new device management policies, adjusting security and control settings according to the specific needs of the organization.
Steps in the Process:
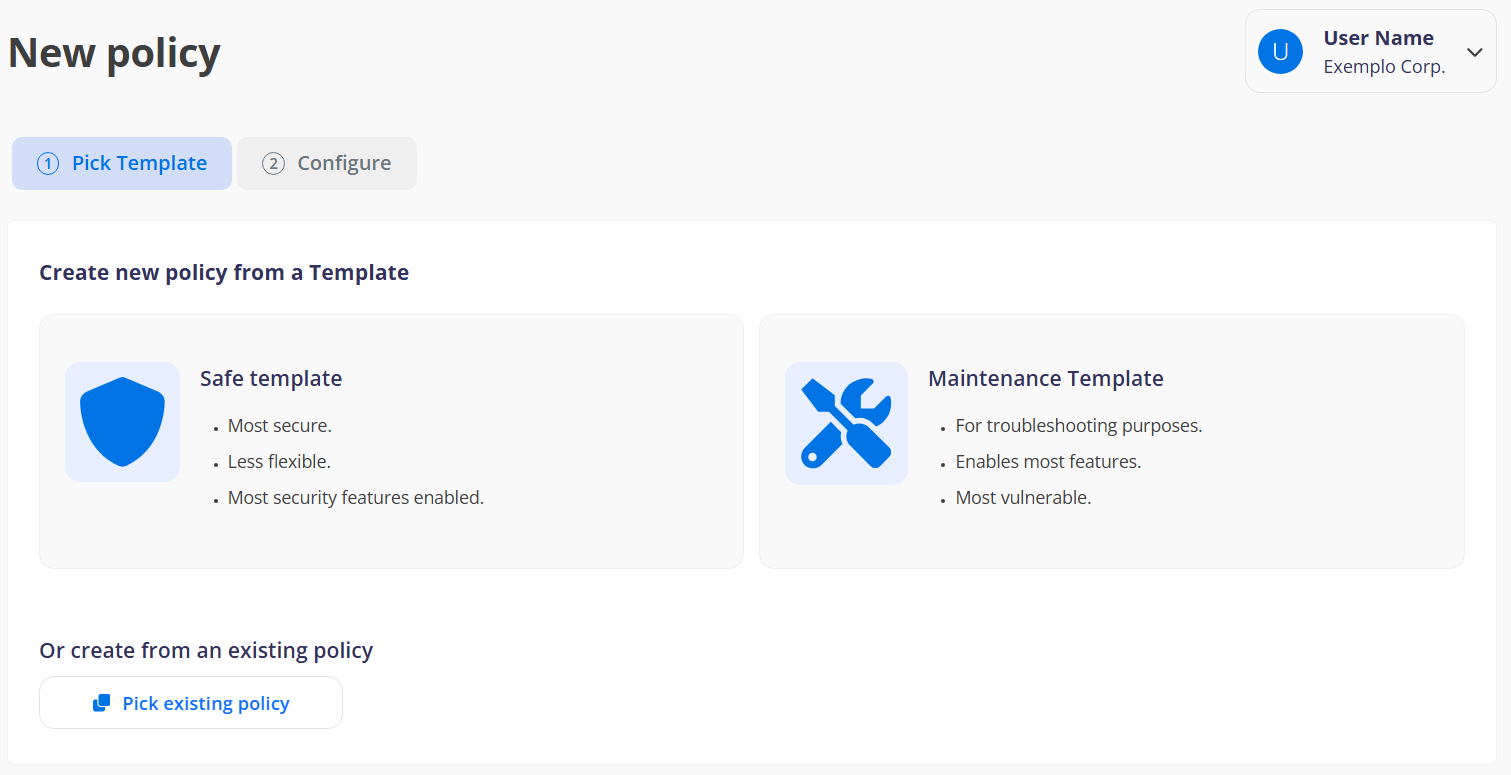
¶ 1 Pick Template
Allows the administrator to select a predefined policy model to begin with.
¶ Available Options
¶ Secure Model
Description: Aimed at environments that require high security. It applies strict policies to protect devices against unauthorized use and improper settings.
Features:
- More secure, with most security features enabled.
- Less flexible, ideal for contexts where strict control is essential.
¶ Maintenance Model
Description: Designed for maintenance and technical support purposes, offering greater freedom of access to device functionalities.
Features:
- Aimed at problem-solving.
- Enables most features, which may increase vulnerability but facilitates maintenance.
¶ Alternative
- Or Crete from an existing policy: The administrator can choose to clone an existing policy, allowing adjustments and customizations based on previously configured policies.

¶ Configure New Policy
- Purpose: After selecting the model, the administrator is guided to configure the details of the new policy.
- Configuration Elements:
- Policy Name: Field to enter a unique and descriptive name for the new policy (20-character limit).
- Policy Group: Selects the group to which the new policy will belong, facilitating the organization and application of similar policies.
- Save and Configure: By clicking this button, the policy is saved, and the administrator is directed to additional detailed configuration steps or to immediately apply the new policy to the devices.
These screens facilitate the creation of customized MDM policies, providing a solid foundation with predefined models that can be quickly adjusted to meet specific security or maintenance requirements, ensuring flexibility and efficiency in managing corporate devices.
¶ Details about the Templates
¶ Secure Template
General Description: This template is designed to ensure a high level of security and control over managed devices. It is ideal for environments that require strict restrictions and centralized control of available functionalities and applications.
Main Configurations:
¶ Applications
Forces the installation of essential applications such as Google Chrome and Nomid Tech apps like tech.nomid.emm.geo and tech.nomid.emm.settings.fastup01.
tech.nomid.emm.settings.fastup01 is configured in KIOSK mode, limiting usage to a specific application with customized settings, including a specific wallpaper, password, and disabling features such as flash.
¶ Permissions and Delegated Scopes
Default permissions are configured to be automatically granted.
Applications have delegated scopes including package access, certificates, system app settings, permission grants, and uninstallation blocking.
¶ Device Features
Various device functionalities are disabled, such as biometrics (fingerprints, facial recognition), Bluetooth settings, beam transmission, outgoing calls, SMS, location sharing, and more.
Advanced security settings like blocking untrusted app installations and enforcing Google Play Protect are enabled.
¶ Additional Security
Requires device encryption, mandatory VPN policies, and strict control over work profile widgets.
Factory reset and user addition are disabled to prevent unauthorized changes.
Features like screen capture, camera use, and account modification are managed to protect sensitive data.
¶ Maintenance Template
General Description: This template is ideal for maintenance and support situations, allowing greater flexibility in device use while maintaining essential security controls.
Main Configurations:
¶ Applications
Provides a set of essential applications, including Google Chrome and Nomid Tech apps like tech.nomid.emm.geo and tech.nomid.emm.settings.fastup01, available for installation but without mandatory KIOSK mode.
Permissions are set to be automatically granted, but with more user-adjustable options.
¶ Permissions and Delegated Scopes
Applications have delegated scopes for package management, certificate settings, system configurations, permission grants, and uninstallation settings.
¶ Device Features
Maintains a moderate level of control over device functionalities, allowing adjustments such as outgoing calls, SMS, and USB file transfers.
Some functionalities, like factory reset, are permitted to facilitate maintenance processes.
Security settings allow more freedom, such as user choices in Google Play Protect adjustments and app update modes.
¶ Additional Security
Game mode, developer, and debugging permissions are allowed to provide a flexible environment for technical support.
System update policy is set to automatic to ensure the device remains up-to-date without manual intervention.
These descriptions help to understand how each template is configured to meet different usage needs, from maximum security with strict control in the "Secure Template" to a more balanced and permissive approach in the "Maintenance Template."
¶ New device
¶ Configure Provisioning
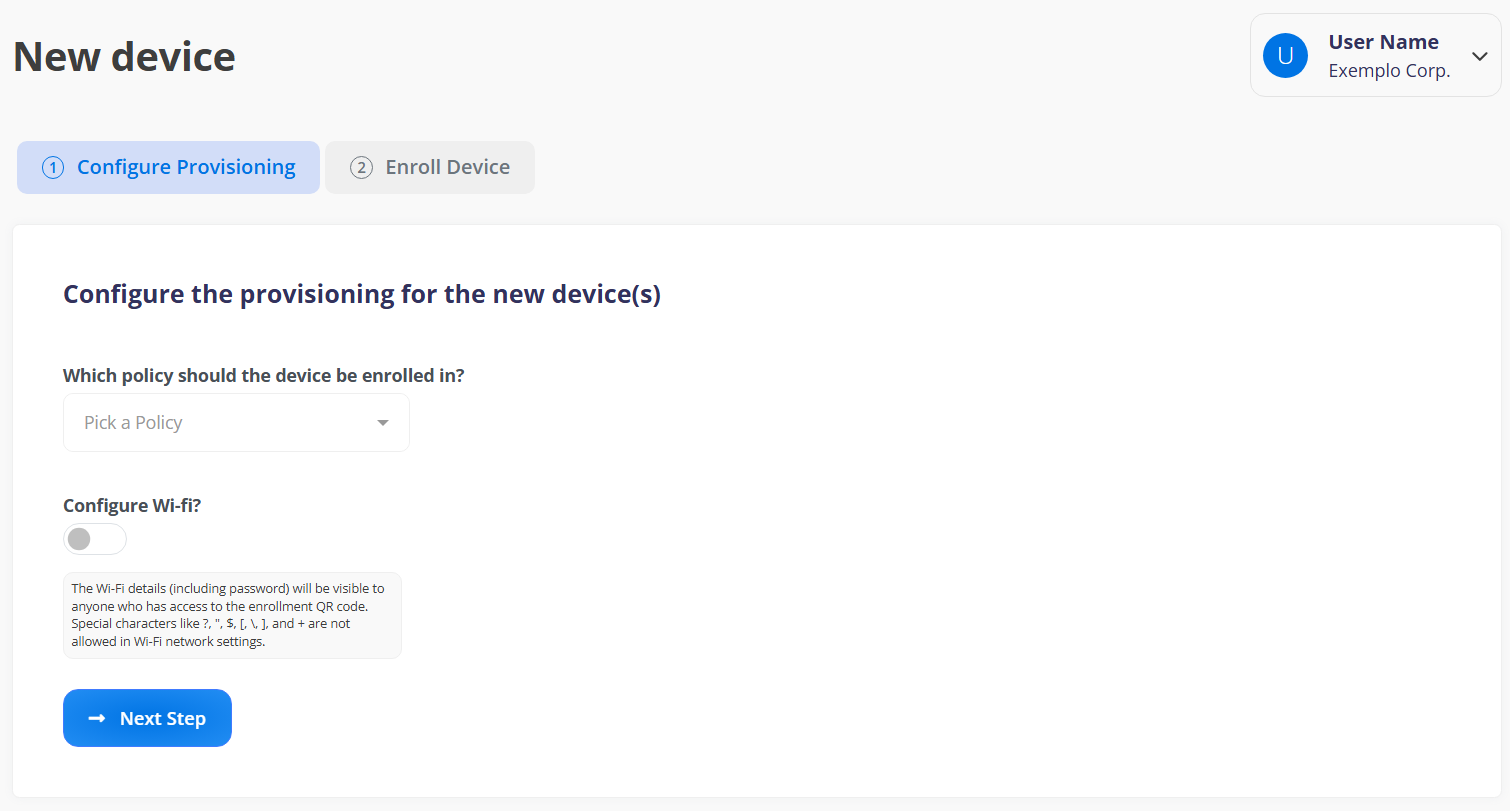
This screen allows you to configure the initial details for provisioning new devices. You can choose a policy for the device, opt to configure Wi-Fi, and then proceed to the next step of registration by clicking "Next Step."
Select a policy:
Click on the "Pick a Policy" box and choose the appropriate policy for the device.
Configure Wi-fi:
Use the toggle button to enable or disable Wi-Fi configuration.
Note: The Wi-Fi details (including password) will be visible to anyone with access to the enrollment QR code.
Click the "Next Step" button to continue to the next step of device registration.
¶ Enroll Device
This screen allows you to enroll a new device by following the instructions and scanning a QR code.
Choose the owner of the device and follow the instructions below:
Then enroll the device to take advantage of all Nomid features.
¶ Enrollment steps
Company Owned:
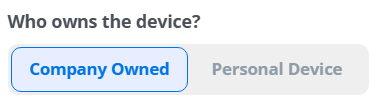
- The camera app will open.
- If the device does not have the QR code reader previously installed, it will be installed automatically:

- Scan the QR code.
- Follow the on-screen instructions.
Personal device:
** Enrollment steps **
- Share the link below with the device to be enrolled and open it
- Link
- If needed, scan the QR Code or enter the code.

QR Code:

Full screen QR code:
Download QR code:
Send enrollment steps to the users via Email:
Send enrollment steps to the users via WhatsApp:
¶ Zero Touch
Zero-touch enrollment is a streamlined process for Android devices to be provisioned for enterprise management. On first boot, devices check to see if they’ve been assigned an enterprise configuration. If so, the device initiates the fully managed device provisioning method and downloads the correct device policy controller app, which then completes setup of the managed device.